
Some of my friends have recently noticed the “snoopers charter” and taken interest on protecting their digital selves. I’m hoping this can help them or anyone else interested on how to accomplish at least a bit of this. Not only is this good to prevent government’s surveying you, but is generally a good idea to be safe online against other malicious entities. So lets dive straight in.
Operating System
As a gamer I know how difficult it is to get away from windows, as such my host machine is windows 10. This is not ideal and as recently disclosed in the NSA leaks (EternalBlue, the WannaCry malware that hit NHS) governments stockpile exploits for windows (and other operating systems). The only real advice that can be offered here is to update everything as often as possible. That includes the main operating system and programs such as Flash and Java.
On Windows 7+ “telemetry data” should be disabled. In “full mode” it collects your browser choice, lists of your peripherals, the apps you use to edit and view images and videos, how long you use the mouse and keyboard, all the applications you’ve ever installed, time spent reading ebooks, text typed in a Microsoft web browser’s address and search bar, URLs visited, visited webpage titles, the words you’ve spoken to Cortana or had translated to text by the system, your ink strokes, and more. A how-to guide on disabling this is available here.
If possible you should run a Linux operating system. Ubuntu is a fairly user-friendly version that is simple to install. But for those heavily privacy conscious a top ten is available here. Although Linux may have vulnerabilities in it, it is patched regularly and is open source, meaning anyone can read the code and fix bugs, the theory being that with that many people maintaining it if backdoors were introduced they would be identified and removed quickly.
If you are stuck with using windows I would recommend only using it for what you need it for but do anything/everything else inside a Linux virtual machine. These are easy and free to setup with programs such as openbox. And being able to create snapshots before installing software or running updates means it’s relatively unlikely that your OS will get broken (just remember to take regular snapshots)
If you are unable to install a secure operating system or virtual machine a boot CD or USB disk may be an option. Here is a guide on installing tails on a live USB with persistent encrypted storage.
Full disk encryption should be enabled. In this day and age there no reason not-to. What this does is secures your data at-rest (when your computer is turned off) and before you type in the password. This is built into windows in the form of bitlocker. If your version doesn’t support it you can always use VeraCrypt. If you are on Linux there is LUKS which is a bit more involved to set up.
Internet Access
So you should now have a secure OS, it’s time for secure communication. The most common and easiest to setup would be a VPN. This acts as a proxy between you and the internet. When using one your connection will look as follows:
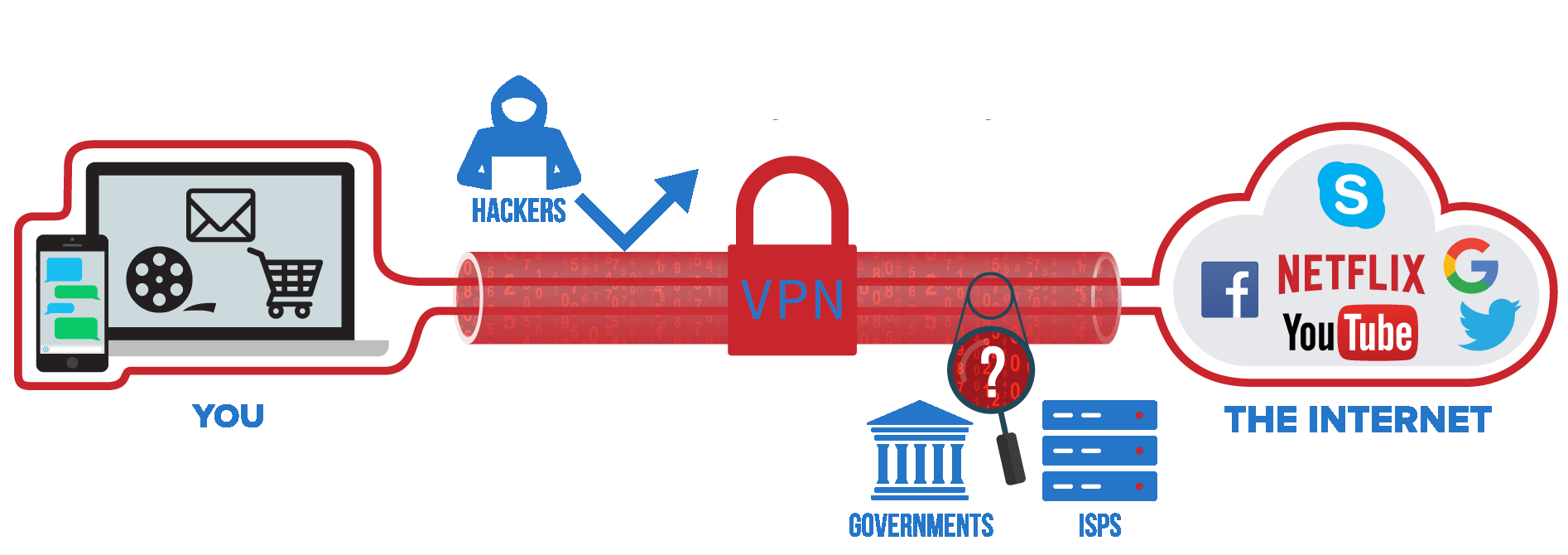
These are fairly cheap, usually around £5 a month. If your motivation includes the snooper’s charter, choose a VPN that is not UK-based, and that does not keep any logs. A list of good VPN services to use is available here.
Along with a VPN you should browse the internet through TOR, setup is simple enough. A link to the TOR browser bundle is available here. Back in the day it used to be super slow, but due to recent events it seems to be a lot quicker and more stable.
Plugins for your browser can also protect you online. If possible you want to disable JavaScript, the plugin “NoScript” can achieve this. However a lot of websites do become virtually unusable without it such as facebook and twitter. For these it is best to set up a whitelist of allowed websites to enable javascript on. Ghostery and AdBlockPlus are great for disabling third party content on websites, this will prevent external companies from tracking you.
You should only be browsing the web and websites using SSL if possible. if you see in the URL bar that the website starts with “https” rather than “http” this indicates that you are using a SSL tunnel. This is similar to a VPN tunnel and ensures encrypted communication between the browser and the web server. There is a plugin called “HTTPS everywhere” which tries to automate this.
Email & Chat
Several email providers offer secure encrypted email solutions. The most popular one is “Protonmail“, however others are available.
Much like email there are messaging applications that use encryption. A list is available here. Chances are you are already using whatsapp, it seems to be well adopted, what you might not know is that you can enjoy secure communications with facebook messenger by using their “secret conversations” feature.
Misc
This should be obvious, but don’t use plain text communications for anything. If you are using FTP move over to SFTP, telnet switch over to SSH. These are more techie things, used by developers or sysadmins and should probably go without saying. You guys should know better!
Use different passwords for each service. Password re-use is the most common way people are compromised. All it takes is 1 website to get owned (linked.in for example) then attackers can lookup your email address, see your password and have access to everything! There are programs to store and even generate passwords for multiple services (lastpass, 1password, dashlane etc.)
If possible you should always enable 2FA (Two Factor Authentication) what this is,for example, is when signing in to a website after you type in your username and password a SMS is sent to you with some random numbers which you then input into the website. If an attacker were to get your username and password they still wouldn’t be able to access the service because they hopefully wouldn’t have your phone. Also this would notify you if someone did try to access your account, which means it’s probably time to change the password!
Well I know this has been a long post, I just hope it has helped someone a little and perhaps increased your online security or at least your knowledge of it. If I have missed anything or you want to add any tips or tricks feel free to leave a comment below.