GitBucket
GitBucket
|
lvl 0 - 6 complete, useful scripts added)
|
|---|
|
|
| ctf_mac.txt 0 → 100644 |
|---|
| enumerate.py 0 → 100755 |
|---|
| enumerate.sh 0 → 100755 |
|---|
| level_04.py 0 → 100644 |
|---|
| load_level.py 0 → 100755 |
|---|
| lvl_00.py 0 → 100755 |
|---|
| lvl_01.py 0 → 100755 |
|---|
| lvl_02.py 0 → 100755 |
|---|
| lvl_03.py 0 → 100755 |
|---|
| lvl_04.py 0 → 100755 |
|---|
| lvl_05.py 0 → 100755 |
|---|
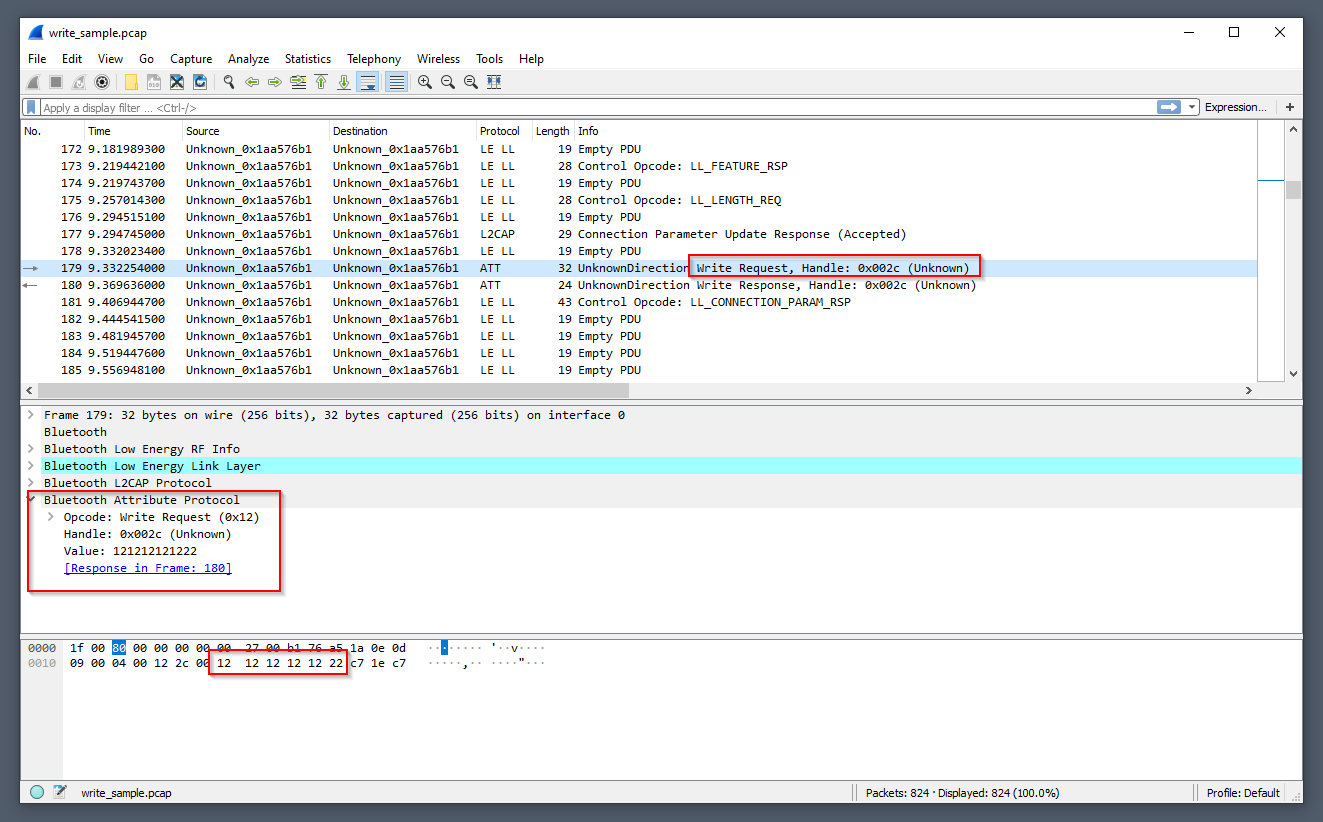
| lvl_05_solution.png 0 → 100644 |
|---|
|
|
| lvl_06.py 0 → 100755 |
|---|
| notes.txt 0 → 100644 |
|---|
| reset_scoreboard.py 0 → 100755 |
|---|
| send2handle.py 0 → 100755 |
|---|
| submit_flag.py 0 → 100755 |
|---|