GitBucket
GitBucket
|
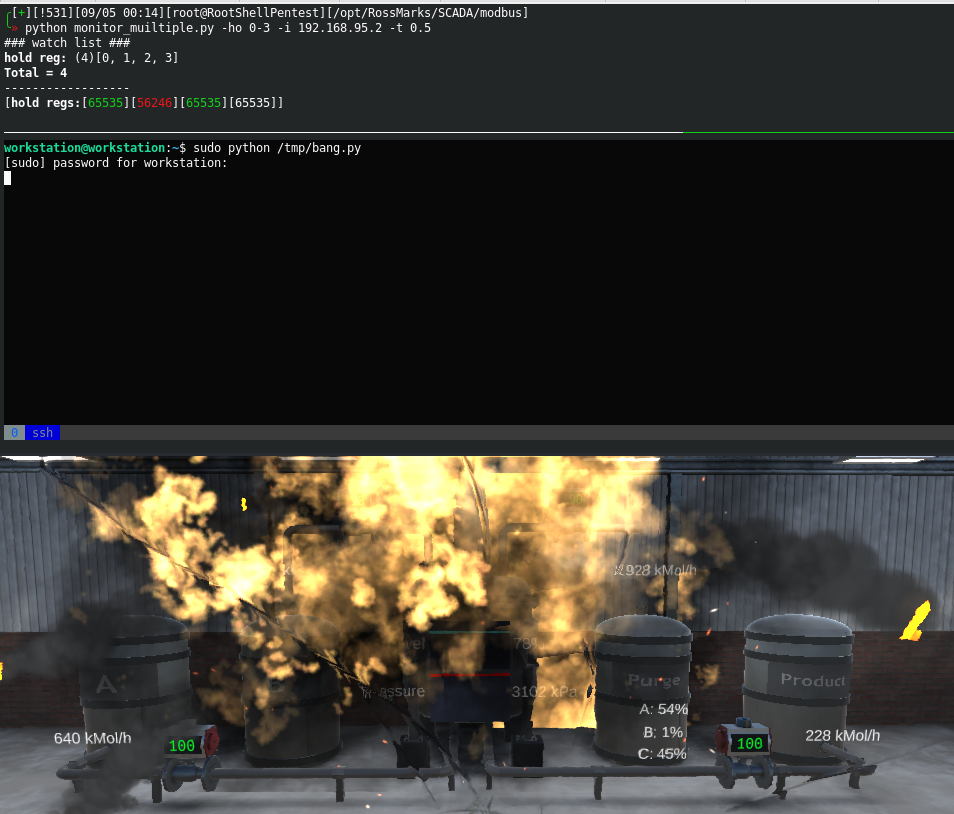
useful scripts and make GRFICS go bang!
|
|---|
|
|
| modbus/GRFICS_bang.png 0 → 100755 |
|---|
|
|
| modbus/GRFICS_bang.py 0 → 100644 |
|---|
| modbus/set_coil.py |
|---|
| modbus/set_reg.py 0 → 100644 |
|---|