I wanted to create a hardware pentesting sample report so when clients ask for a sample report I’m not giving them a web app one and saying “It’s like this but different”. I knew a cheap router from china would likely be insecure and make for a good report, I didn’t expect just how bad it would be! I bought the following router:
A £6 router! how is that even possible! Anyway, lets get started:
Stage 1: Preparing for Testing
Before any testing began, the device was examined to confirm it was functioning properly. Network activity was monitored using packet sniffing tools to detect any automatic firmware downloads or suspicious traffic. No unauthorised downloads were detected, suggesting a reasonable initial defence against remote attacks.
Stage 2: Physical Examination
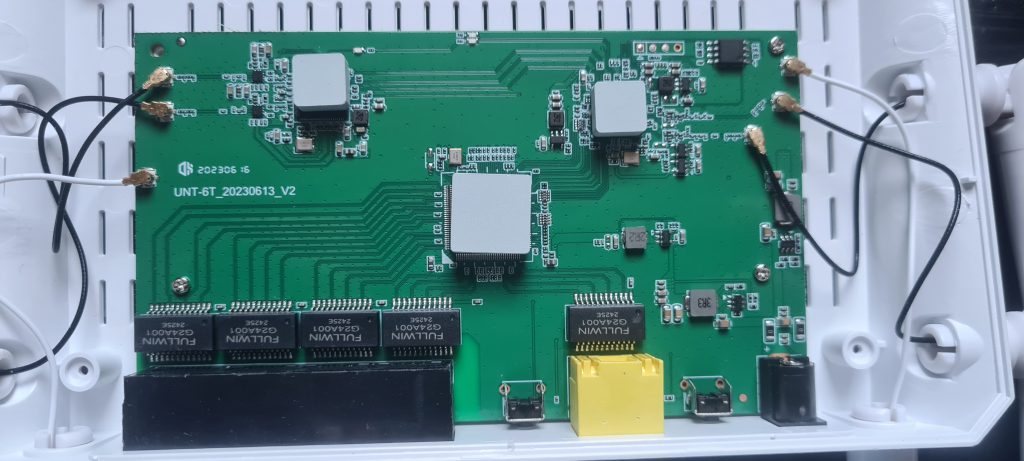
The device was opened to inspect its internal components. This revealed various chips and debug interfaces that were crucial for deeper analysis. However, the chips had no identifying markings, making it impossible to find datasheets at this stage. Additionally, there was no FCC ID, which further limited available information on the components.
Stage 3: Accessing the Debug Console
Attention was turned to the RS232 debug port (top right of previous image). By connecting to this port, access was gained to the device’s debug console. This provided valuable insights into its operations and capabilities, revealing potential areas for further testing.
Stage 4: Extracting and Modifying Firmware
Attempts to access the flash chip’s contents using an inline clip were unsuccessful. The chip was removed from the PCB, and a socket was installed to enable quick removal and replacement for debugging.
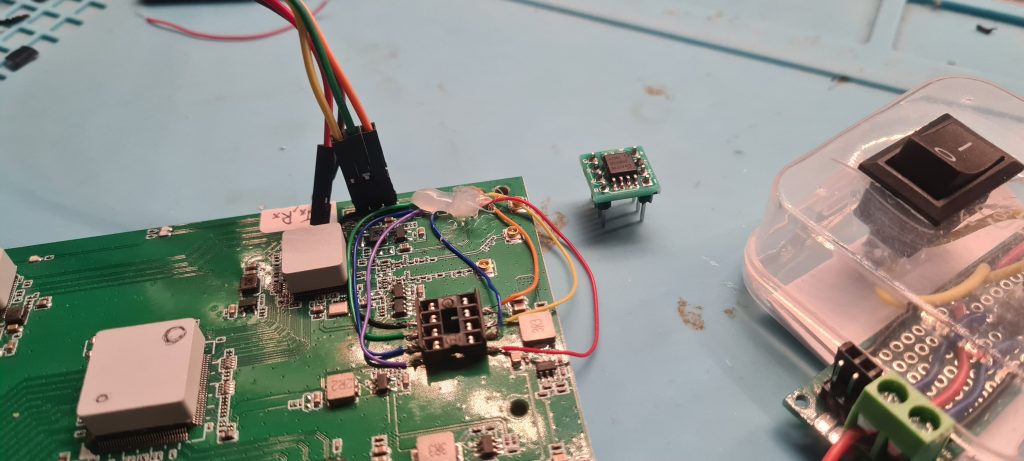
Stage 5: Iterative Testing Process
The testing process was not strictly linear, previous steps were revisited based on new findings. Each discovery influenced the next phase of testing, ensuring a thorough evaluation of the device’s security.
Stage 6: Modifying and Re-Flashing the Firmware
In one of the final steps, the extracted firmware and bootloader were modified before being re-flashed onto the chip. This confirmed that unauthorised firmware changes were possible, posing a serious security risk. This test was performed last due to the high chance of bricking the device, which could have prevented further testing.
Issues Identified
The most likely aspect to be looked at by an attacker is the web interface as this would typically be the place an attacker has easy access to. The first thing I did after logging in was set the password to a single letter, yup could still log in with that so there is clearly no password policy. I then set it to “test”:
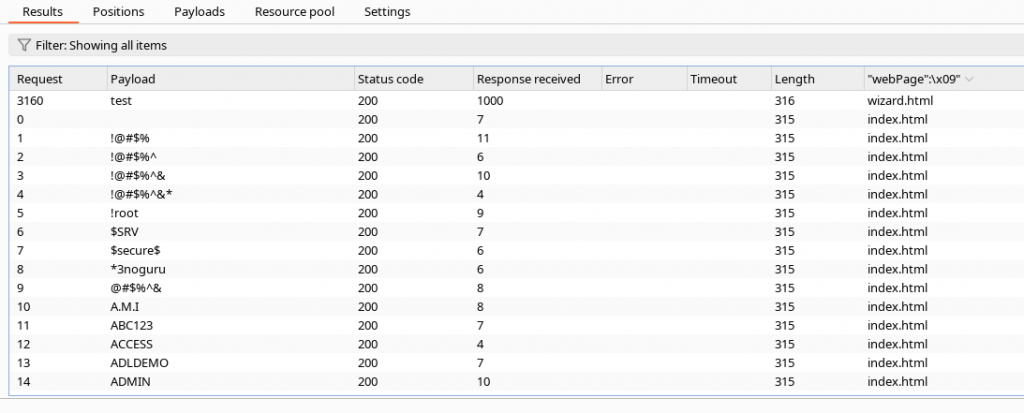
Of course theres no brute-force protection. Even worse, I could just browse to /wizard.html and there was no session checking whatsoever! as long as you know the endpoint you can browse to it and change the routers settings unauthorized. The “logout” button simply redirects to “index.html” which contains the login form.
It is worth mentioning here that along with the terribly coded/modified files the developer intended you to use to configure the device, lots of old files (oldbakhome.htm, countDownPage_old.htm) and Realtek default debug files and scripts were left on the device and were accessible and usable. Some of these disclosed the development environment used and paths on the dev’s computers. The device logs all wireless access points in the vicinity and devices that have connected to it including the mac address and device name. It appears these logs have not been wiped before manufacture and include developer devices used when creating and testing this router:
{
"idx": "1",
"ip": "192.168.0.19",
"mac": "D6:6D:0F:7D:1C:FA",
"type": "2",
"linkType": "white",
"osType": "2",
"name": "dongcaikiiPhone"
}, {
"idx": "2",
"ip": "192.168.0.7",
"mac": "34:12:F9:72:6A:EA",
"type": "2",
"linkType": "white",
"osType": "1",
"name": "Honor_10_Lite-648f73255de"
}, {
"idx": "3",
"ip": "192.168.0.10",
"mac": "A8:9C:ED:9A:1F:10",
"type": "2",
"linkType": "white",
"osType": "1",
"name": "MI9-winnie"
}
If you did want to know the password (perhaps the admin is using it elsewhere on the network) then use the “backup settings” feature to read it in plaintext. As demonstrated below you can clearly see the admin username of “admin” and the password of “SuperSecretPassword”:
$> curl http://192.168.168.1/config.dat | head
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
COMPCS%��6g03�������������� 0 0 0 --:--:-- --:--:-- --:--:-- 0
�����d������w
100 9721 �$
�_�O��-Rd����00G/d
e��;fg?�j��j|admin����SuperSecretPassword� ���
0kW��`/#/5/G/
�O��w/�/�/�/�/�/Z#�f/�/? ?2D?V?Z#��/�?�?�?�?�?�?Z#�p?O▒O *O<ONO`OZ#��?�O@�O�O�O�O�OZ#�zO�_"_4_F_X_j_Z#�k]
��TU��T��T��T��T���Q.
�T��T�T�T�T��R��T �T
97��T
�T
�R��T�T�T�T��T�T��R�a!窄R�a!��R�a!���R��R��R�)�p_�oZ#��o�oX%
�x�o�o/z|8|�ZQ,��R�-���R��v��R�-il,m�O�O���O��]�?��?��0�*�<�N�`�r���
21��O�����Џ�����/��Q�K�sLM�@A<�N�`�
USz�Tz�U��W���V x�j�����$��O.x��O.y�p��R�O.wzZ#{=��] |
S*}~▒�~30▒��1490W�O���▒O��O0 1�/�@0.��.▒���
���ƿ▒�<,�
Speaking of hardcoded passwords they were everywhere. After pulling the unencrypted firmware from the flash chip, it was easy to find JSON files containing credentials, shadow files, private keys, smbpassword file, etc. the hardcoded web app login password and wireless password were on a sicker on the router’s case. Not that you needed a password for access.
The router had telnet enabled by default. When trying to login with an non-existing username it asked for a password, however when trying to log in as root:
$> telnet 192.168.168.1 23
Trying 192.168.168.1...
Connected to 192.168.168.1.
Escape character is '^]'.
rlx-linux login: admin
Password:
Login incorrect
rlx-linux login: root
RLX Linux version 2.0
_ _ _
| | | ||_|
_ _ | | _ _ | | _ ____ _ _ _ _
| |/ || |\ \/ / | || | _ \| | | |\ \/ /
| |_/ | |/ \ | || | | | | |_| |/ \
|_| |_|\_/\_/ |_||_|_| |_|\____|\_/\_/
For further information check:
http://processor.realtek.com/
# ls
bin etc init mnt root tmp var
dev home lib proc sys usr web
That is root access without a password enabled by default!
I then tried to modify the firmware and flash it back onto the chip, suprisingly there was a signature checksum that was failing since the firmware had changed, so I attempted to change the bootloader. This was possible however I didnt have time to work out how to either “NOP-out” the checksum comparison or work out how to generate a new checksum and put that into the bootloader. By default reading the output from UART the device responds:
Booting... init_ram M init ddr ok DRAM Type: DDR2 DRAM frequency: 533MHz DRAM Size: 128MB JEDEC id C84017, EXT id 0xc840 found gd25q64 flash vendor: GigaDevice gd25q64, size=8MB, erasesize=4KB, max_speed_hz=41000000Hz auto_mode=0 addr_width=3 erase_opcode=0x00000020 =>CPU Wake-up interrupt happen! GISR=89000004 ---Realtek RTL8197F boot code at 2019.04.24-03:30-0700 v3.4.11d-CMCC-pre5 (999MHz) no sys signature at 00010000! no sys signature at 00020000! Jump to image start=0x80a00000... decompressing kernel: Uncompressing Linux... done, booting the kernel.
The text “Pwned by Ross Marks” was modified from the original text “Realtek RTL8197F” in the following UART output by modifying the bootloader and flashing it onto the chip:
Booting...
init_ram
M init ddr ok
DRAM Type: DDR2
DRAM frequency: 533MHz
DRAM Size: 128MB
JEDEC id C84017, EXT id 0xc840
found gd25q64
flash vendor: GigaDevice
gd25q64, size=8MB, erasesize=4KB, max_speed_hz=41000000Hz
auto_mode=0 addr_width=3 erase_opcode=0x00000020
=>CPU Wake-up interrupt happen! GISR=89000004
---- Pwned by Ross Marks ---- at 2019.04.24-03:30-0700 v3.4.11d-CMCC-pre5 (999MHz)
no sys signature at 00010000!
no sys signature at 00020000!
Jump to image start=0x80a00000...
decompressing kernel:
Uncompressing Linux... done, booting the kernel.
Challenges in Reporting the Vulnerabilities
One of the difficulties I encountered was the inability to obtain any CVE’s for the security issues I discovered. Normally, CVEs are assigned to known manufacturers and vendors, providing a way to track and address vulnerabilities. However, in this case, I was unable to identify a manufacturer for the device, making it impossible to report these issues through official channels. Without a clear vendor, there is no established process to ensure these flaws are acknowledged or patched, leaving the device vulnerable to exploitation with no accountability.
Conclusion
The device is not suitable for use and presents a major security risk. The number and severity of the issues mean that it cannot be trusted to protect sensitive information or maintain secure operations. Any organization or individual using this device would be exposing themselves to significant dangers, including data theft, system compromise, or even full control of the device by an attacker. Without urgent fixes, using the device in any professional or critical setting would be highly irresponsible, as it could easily be exploited.