
 GitBucket
GitBucket
Challenge 2: "Echo Chamber"
Following the success of your first infiltration, you've intercepted another device from the same syndicate. This one seems almost identical — same pinout, same behavior — but something’s off. Your usual tools can’t make sense of the UART output. It looks like the engineers behind this one were clever enough to obfuscate communication by using a non-standard baud rate.
The challenge is a test of patience and precision. You'll need to analyze the signal itself to get in.
Your mission is clear:
- Identify the UART pins using your probing tools.
- Determine the correct (non-standard) baud rate via signal analysis.
- Establish a reliable terminal connection and extract the flag from the interface.
Setup
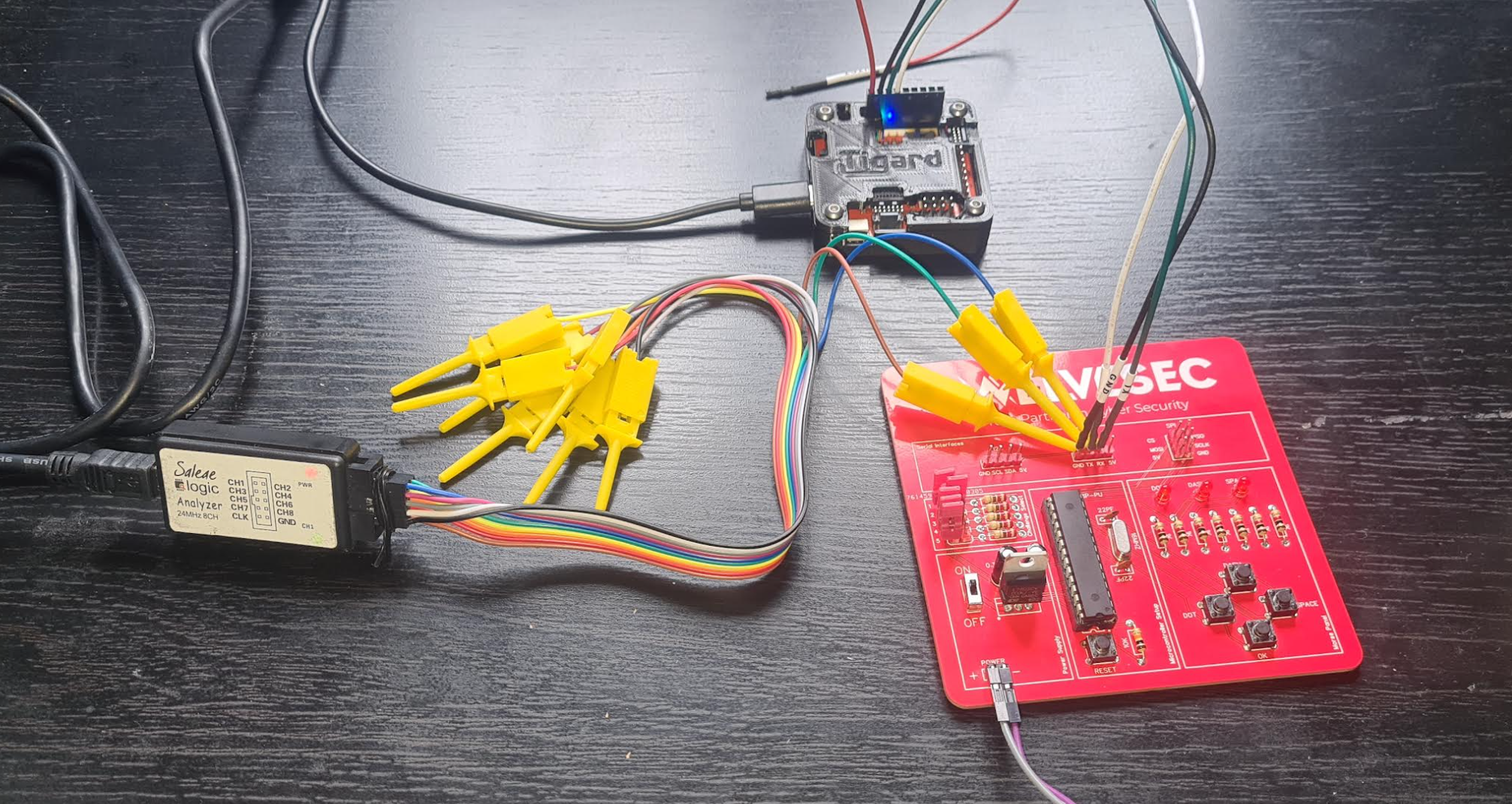
Notes
I started by running logic to capture the transmissions with the logic analyser
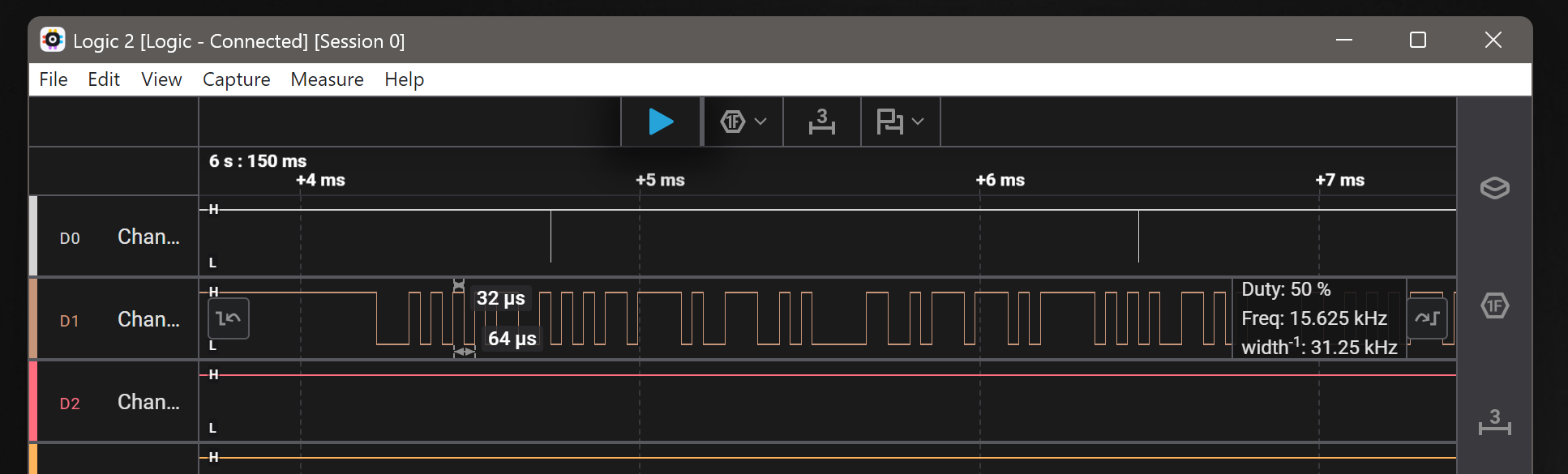
Some simple math to determine the baud rate from the pulse width: (or ask chatGPT like I did)
Baud rate calculation
Given: Bit duration = 32 microseconds = 32 × 10⁻⁶ seconds
Formula: Baud rate = 1 / bit duration
Calculation: Baud rate = 1 / (32 × 10⁻⁶)
Baud rate = 31,250 baud
Answer: 31,250 baud
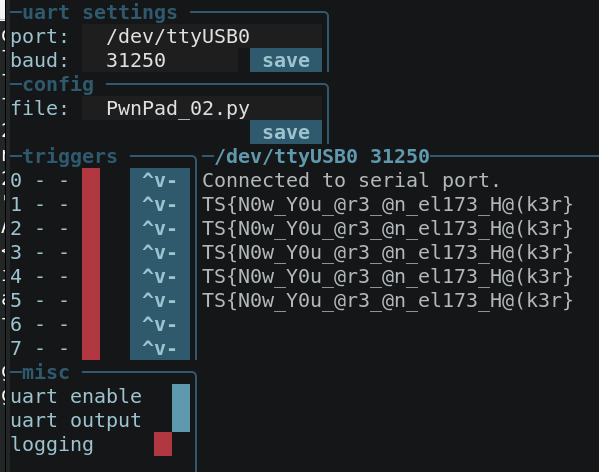
Whip up a quick glitch-o-bolt config: 02_GoB_config.py
This results in:
This could also be checked direcectly in logic:
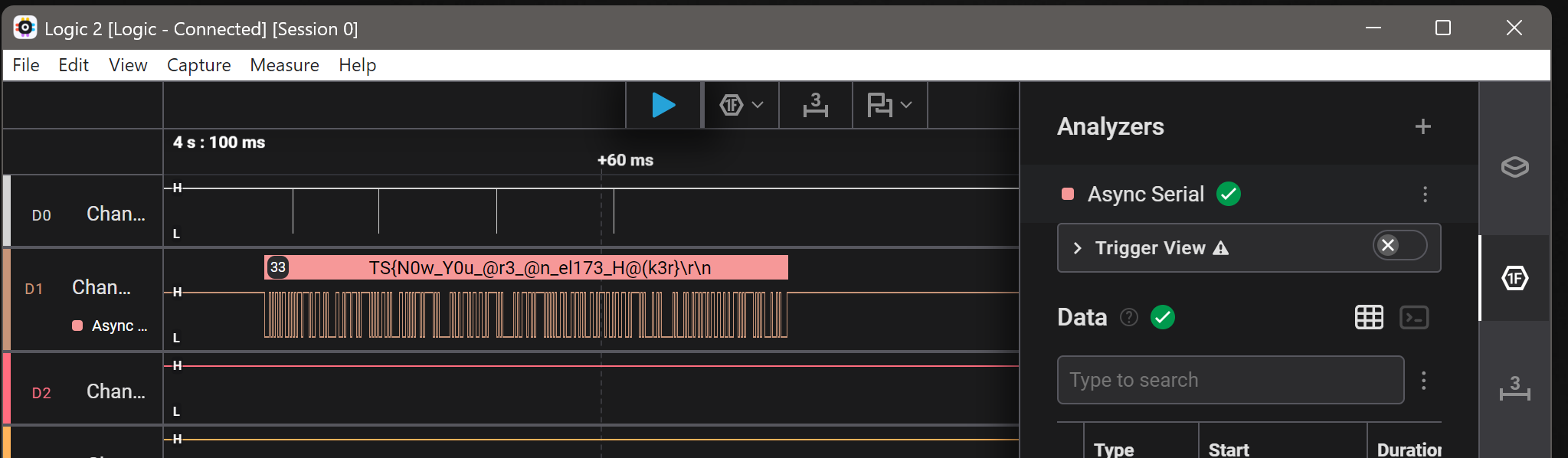
(Reading source I know the baud rate is supposed to be 31337)