
 GitBucket
GitBucket
Challenge 4: "Invisible Wires"
You’ve infiltrated a secure facility to extract a prototype device believed to hold critical secrets. After ripping the main board from its casing and making your escape, a sudden realization hits (you left a secondary board behind), still wired in and powered.
Unexpectedly, the stolen board is trying to communicate with its twin over I2C, as if expecting a response. It’s time to turn the tables: tap into the bus, reverse the dialogue, and extract what it’s trying to say.
Your mission is clear:
- Identify the I2C lines used for board-to-board communication.
- Reverse engineer the protocol or expected responses from the second board.
- Emulate or spoof the missing board to trigger a flag or secret message.
Setup
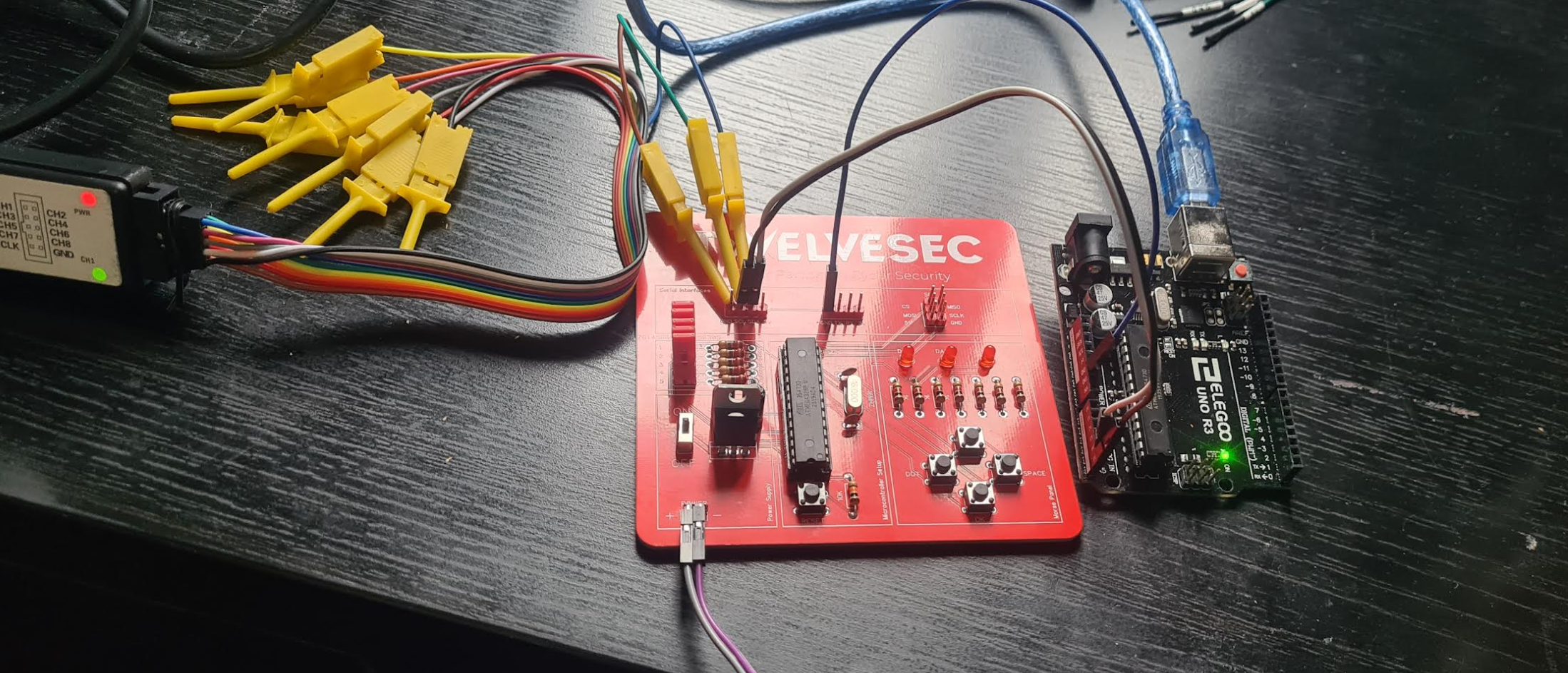
Notes
Fire up the logic analyzer and see it's lookign for a device with a specific address:
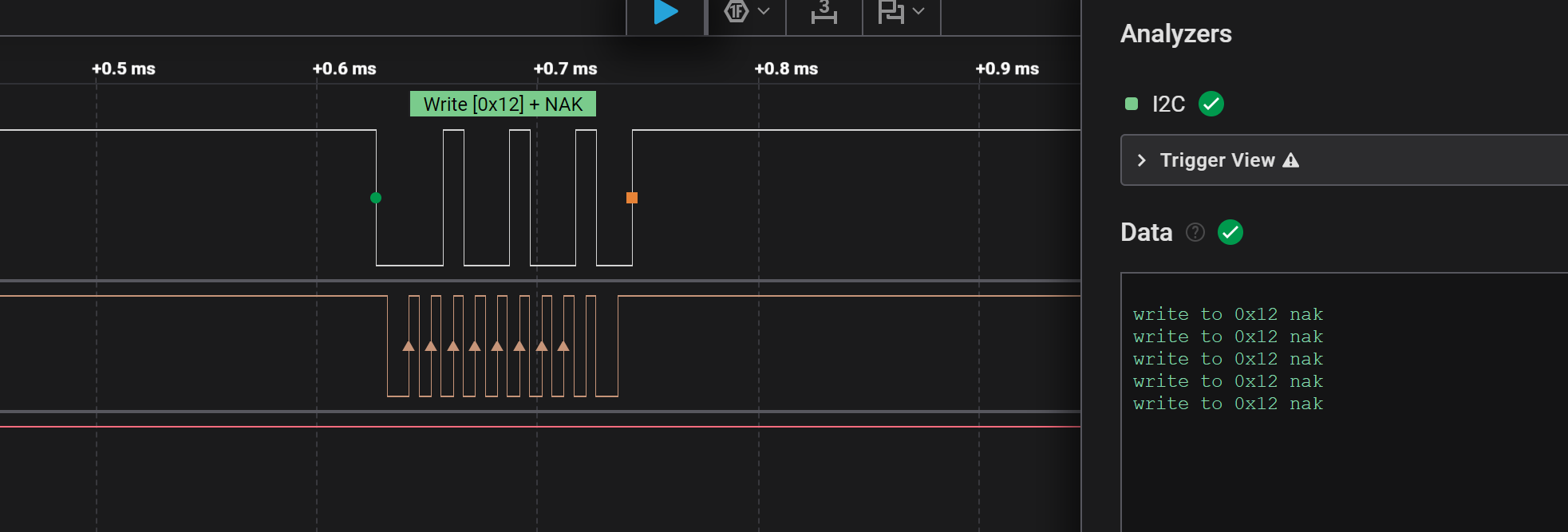
So I made a small arduino sketch to emulate this: 04_arduino.ino
The next time I checked the logic analyzer:
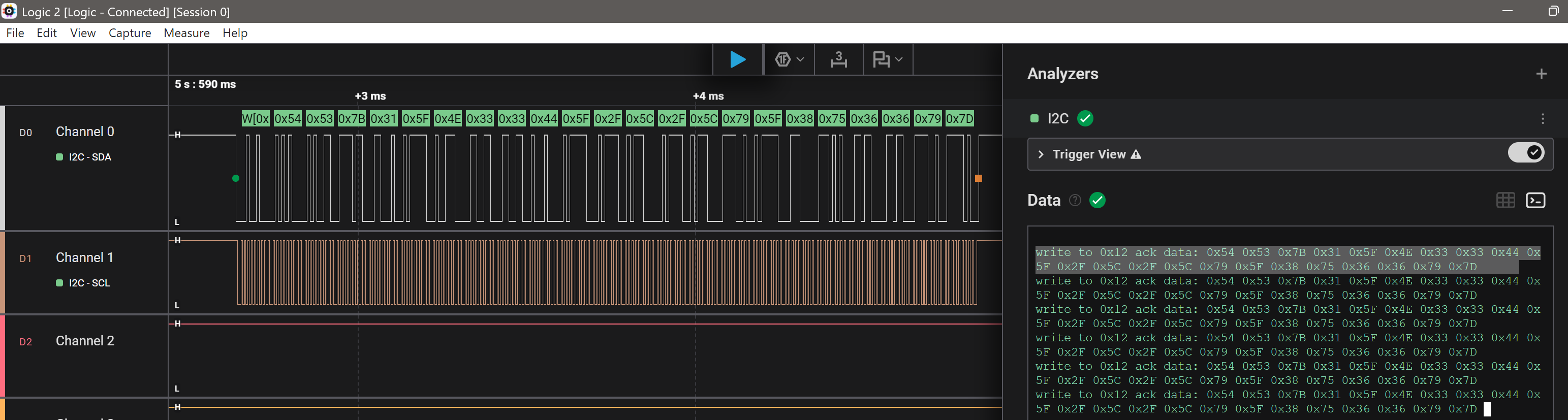
This decodes to:
TS{1_N33D_/\/\y_8u66y}