GitBucket
GitBucket
Challenge 5: "Code Heist"
In a high-tech underground bunker, you've stumbled upon a security keypad linked to a classified device. The rumors suggest that entering a hidden password will unlock a secret mode, but there’s a catch—the password isn’t documented anywhere.
However, your investigation reveals that the device’s firmware is stored in the internal Flash memory, and there’s a chance that the password is hardcoded within. If you can extract the firmware, you just might be able to pull off the ultimate code heist.
Your mission is clear:
- Dump the firmware from the internal Flash memory using available debugging or ISP interfaces.
- Analyze the firmware binary to locate and recover the hardcoded password.
- Use the password on the keypad to unlock the device’s secret mode and retrieve the flag.
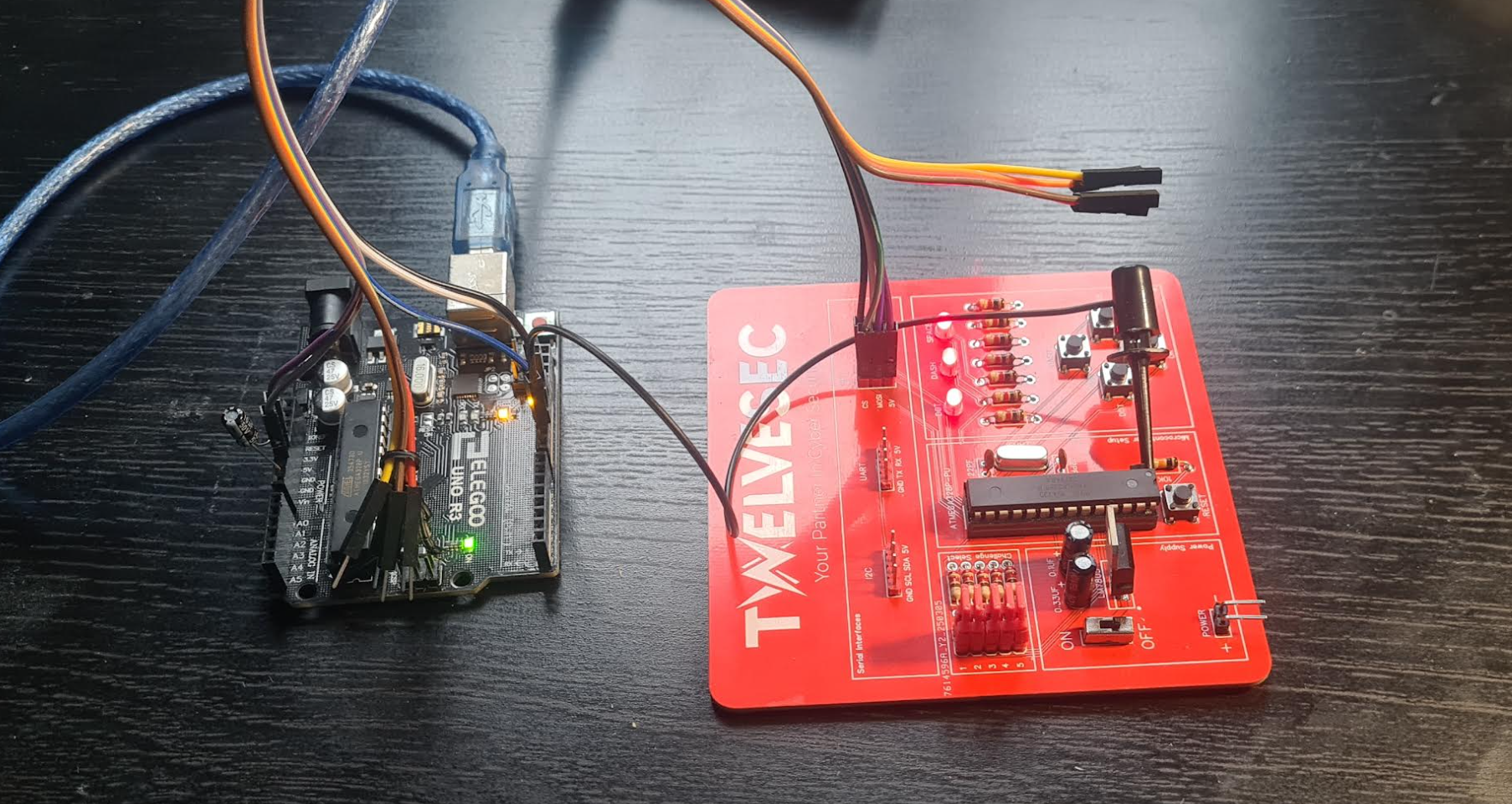
Setup
Notes
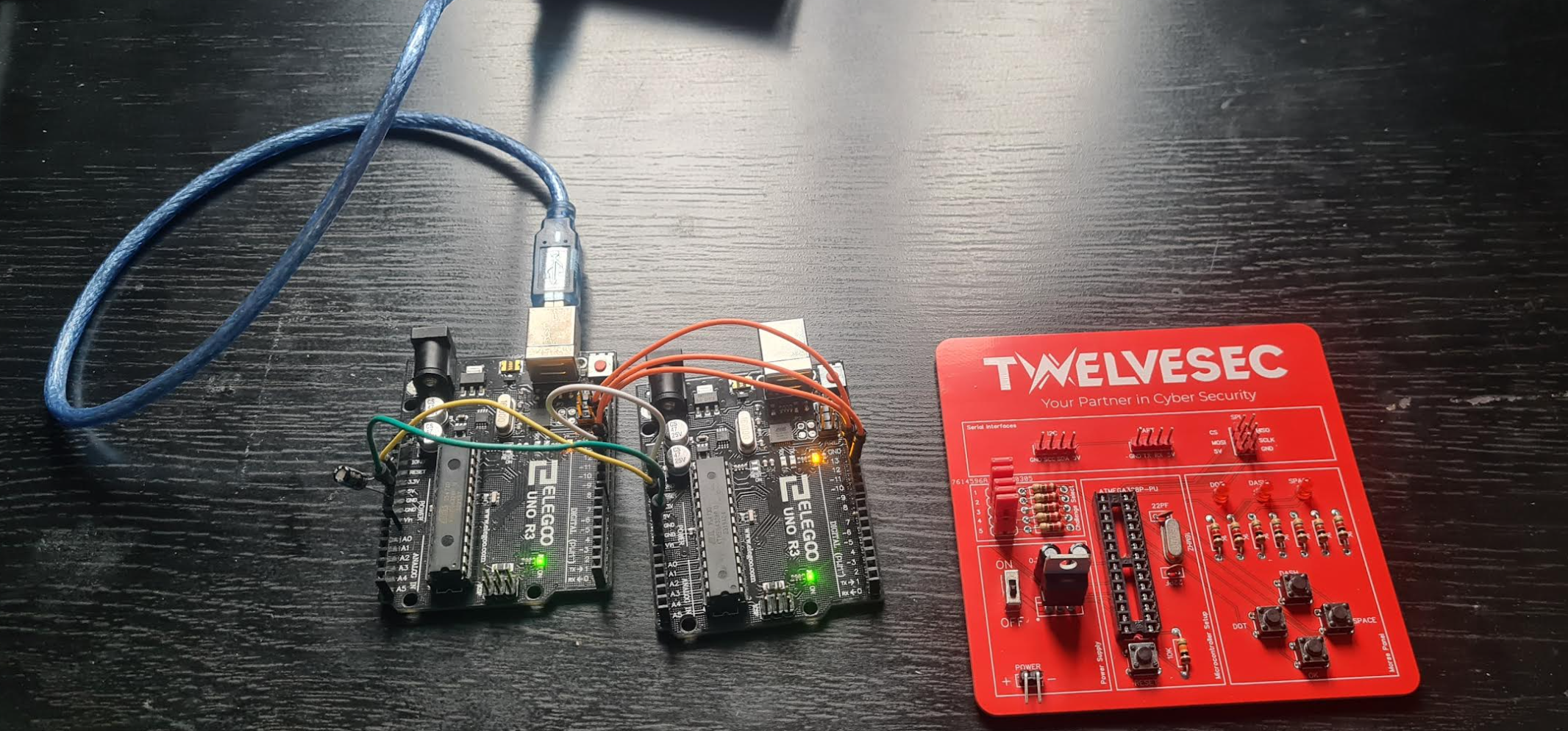
I used a seperate arduino with the "Arduino as ISP" sketch loaded and pulled the chip from the PwnPad which was then put in to a second spare arduino. The following was used to confirm that the atmega328p could be read:
$> avrdude -v -c arduino -P /dev/ttyACM0 -b 19200 -p m328p -n
avrdude: Version 7.1
Copyright the AVRDUDE authors;
see https://github.com/avrdudes/avrdude/blob/main/AUTHORS
System wide configuration file is /etc/avrdude.conf
User configuration file is /root/.avrduderc
User configuration file does not exist or is not a regular file, skipping
Using Port : /dev/ttyACM0
Using Programmer : arduino
Overriding Baud Rate : 19200
AVR Part : ATmega328P
Chip Erase delay : 9000 us
PAGEL : PD7
BS2 : PC2
RESET disposition : possible i/o
RETRY pulse : SCK
Serial program mode : yes
Parallel program mode : yes
Timeout : 200
StabDelay : 100
CmdexeDelay : 25
SyncLoops : 32
PollIndex : 3
PollValue : 0x53
Memory Detail :
Block Poll Page Polled
Memory Type Alias Mode Delay Size Indx Paged Size Size #Pages MinW MaxW ReadBack
----------- -------- ---- ----- ----- ---- ------ ------ ---- ------ ----- ----- ---------
eeprom 65 20 4 0 no 1024 4 0 3600 3600 0xff 0xff
flash 65 6 128 0 yes 32768 128 256 4500 4500 0xff 0xff
lfuse 0 0 0 0 no 1 1 0 4500 4500 0x00 0x00
hfuse 0 0 0 0 no 1 1 0 4500 4500 0x00 0x00
efuse 0 0 0 0 no 1 1 0 4500 4500 0x00 0x00
lock 0 0 0 0 no 1 1 0 4500 4500 0x00 0x00
signature 0 0 0 0 no 3 1 0 0 0 0x00 0x00
calibration 0 0 0 0 no 1 1 0 0 0 0x00 0x00
Programmer Type : Arduino
Description : Arduino for bootloader using STK500 v1 protocol
Hardware Version: 2
Firmware Version: 1.18
Topcard : Unknown
avrdude: AVR device initialized and ready to accept instructions
avrdude: device signature = 0x1e950f (probably m328p)
avrdude done. Thank you.
Then pull the firmware:
$> avrdude -c arduino -P /dev/ttyACM0 -b 19200 -p m328p -U flash:r:flash_dump.bin:r avrdude: AVR device initialized and ready to accept instructions avrdude: device signature = 0x1e950f (probably m328p) avrdude: reading flash memory ... Reading | ################################################## | 100% 20.92 s avrdude: writing output file flash_dump.bin avrdude done. Thank you.
Instead of loading the firmware in ghidra or another reversing tool I simply ran strings against it to find some low hanging fruit:
$> strings flash_dump.bin
h>s@
/_?O/s3'
IUZO
E+F+G+i
/_?Oy
h1P
!P1 A Q V
#+$+%+y
G.Q,a,q,
E.Q,a,q,
C.Q,C
d.q,N
O.Q,a,q,
&.1,s
G.Q,
n.q,N
/_?OY
(P1
.P1
'*0Q
?OOO_O
"P1 9
N__O$
N__O
"P1
Q,A,
APP@
SECRET MODE UNLOCKED: TS{F1rmw@re_S3cret}
- .-- ...-- .-.. ...- . ..... ...-- -.-.
+=========== Welcome To The UART Challenge ===========+
| You Successfully Identified The Baudrate |
| You Can Now Control The LEDS |
| TS{U@rt_15_@w3s0m3} |
+=====================================================+
SELECT LED (1/2/3) >
Error Wrong Id !
SELECT STATUS (0/1) >
Something Went Wrong!
TS{N0w_Y0u_@r3_@n_el173_H@(k3r}
TS{(h@||eng3_07P_i5_
TS{1_N33D_/\/\y_8u66y}
I will never tell you my secret !
TS{Gl1th3s_@r3_Awe50m3_!}
---------------------
cnt:
Hahaha, I changed my trigger go and find it
TS{0h_n0_y0u_foun6_my_7r1gg3r}
You will never enter my vault!
TS{Y0u_3nter36_th3_v@ul7}
You are no good enough
TS{D@mn_y0u_@r3_g006}
Welcome to my Login Interface!
You managed to identify my UART baudrate, now please login.
[+] Please Provide Your Password:
Please Enter Your 8 Digit PIN:
TS{D0n7_M355_w17h_t1m3}
[-] Wrong PIN!
No Challenge Selected!
[-] Login FAILED
TS{L0gin_Succ355fu1_!}
d3@1bt7*0PqSxc9~^
25315294
355fu1_!}
[-] Login FAILED
- .-- ...-- .-.. ...- . ..... ...-- -.-.
d3@1bt7*0PqSxc9~^
25315294
Password:
Please Enter Your 8 Digit PIN:
TS{D0n7_M355_w17h_t1m3}
[-] Wrong PIN!
No Challenge Selected!
[-] Login FAILED
TS{L0gin_Succ355fu1_!}
- .-- ...-- .-.. ...- . ..... ...-- -.-.
d3@1bt7*0PqSxc9~^
25315294
$N__O
Wow loads of flags! we know that we need to find the morese code as that can be input via UART:
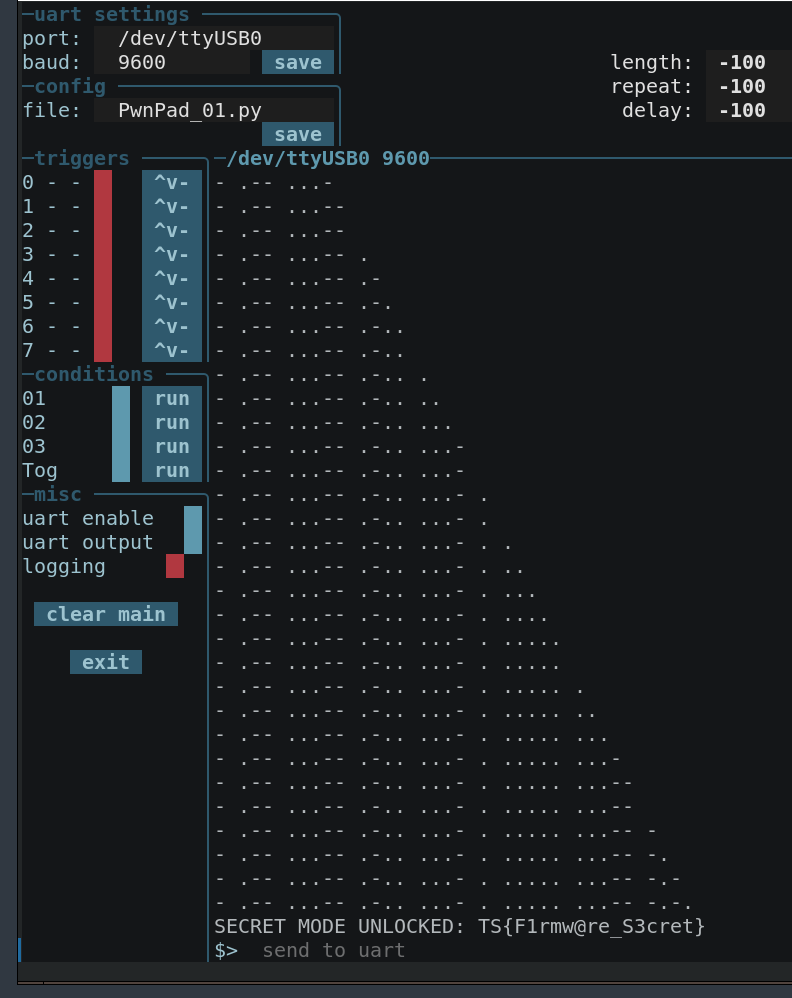
I wasnt convinced that was the intended way of doing it, so I also pulled the firmware using the headers on the board, that setup looked like: