GitBucket
GitBucket
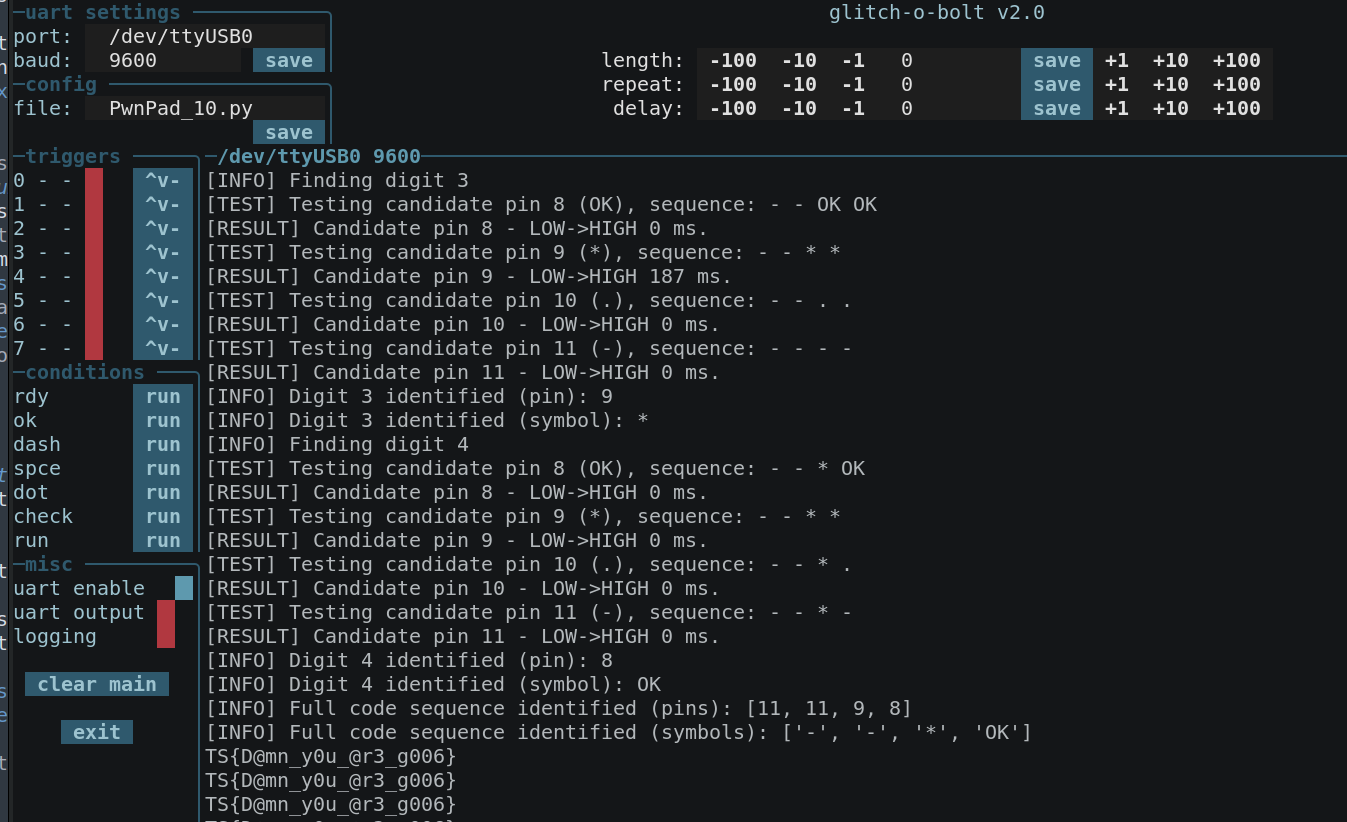
Challenge 10: "Tempo Leak"
This challenge builds on the mechanics of Clock Spy, but with a twist. The device now uses a 4-digit PIN, and the password verification is only triggered after all four digits have been entered.
Your goal remains a timing side-channel attack to recover the PIN. The change in input handling means you’ll need to adjust your analysis techniques accordingly.
Your mission is clear:
- Capture and analyze timing data during the full 4-digit PIN entry.
- Leverage timing variations to deduce the complete PIN.
- Recover the PIN and bypass the security check.
- Retrieve the flag via UART at 9600 baud rate.
Setup
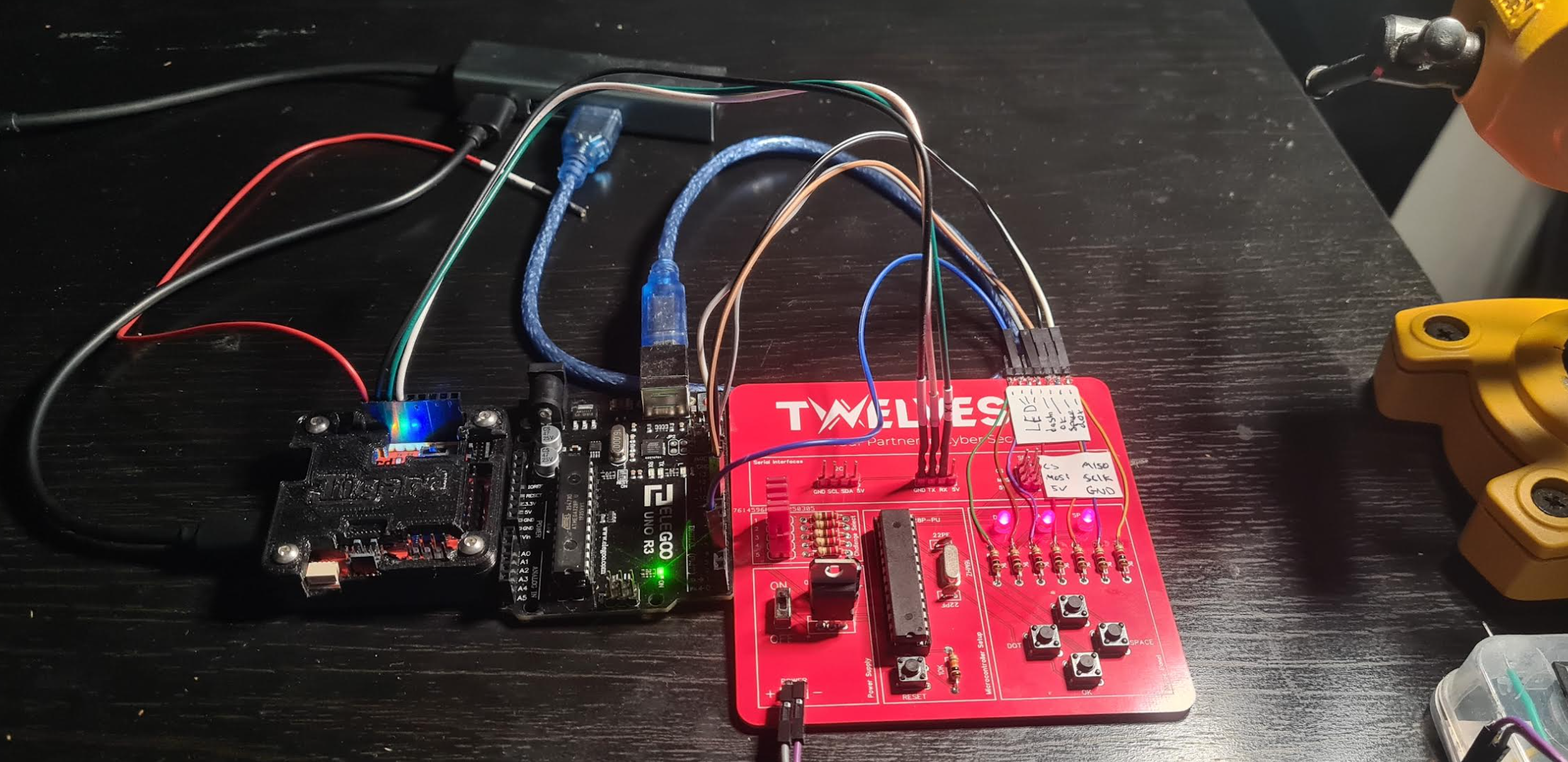
Notes
This was very similar to the previous one. Minor tweaks to the glitch-o-bolt config: 10_GoB_config.py