GitBucket
GitBucket
Challenge 11: "Chaos Chain: Glitchgate"
Welcome to the Glitchgate arena, where you get no schematics, no source code, and only the bare device in front of you. Your goal is to break in by chaining multiple hardware attack techniques.
This challenge combines two major hurdles:
- An obscure UART baud rate that you must identify to establish communication.
- A fault injection attack that bypasses the UART login screen, granting unauthorized access.
You’ll need to carefully analyze the device, discover the correct UART settings, and time your glitch precisely to defeat its defenses.
Your mission is clear:
- Identify the obscure UART baud rate used by the device.
- Bypass the UART login screen via a fault injection.
- Gain control of the device and retrieve the flag through the UART interface.
Setup
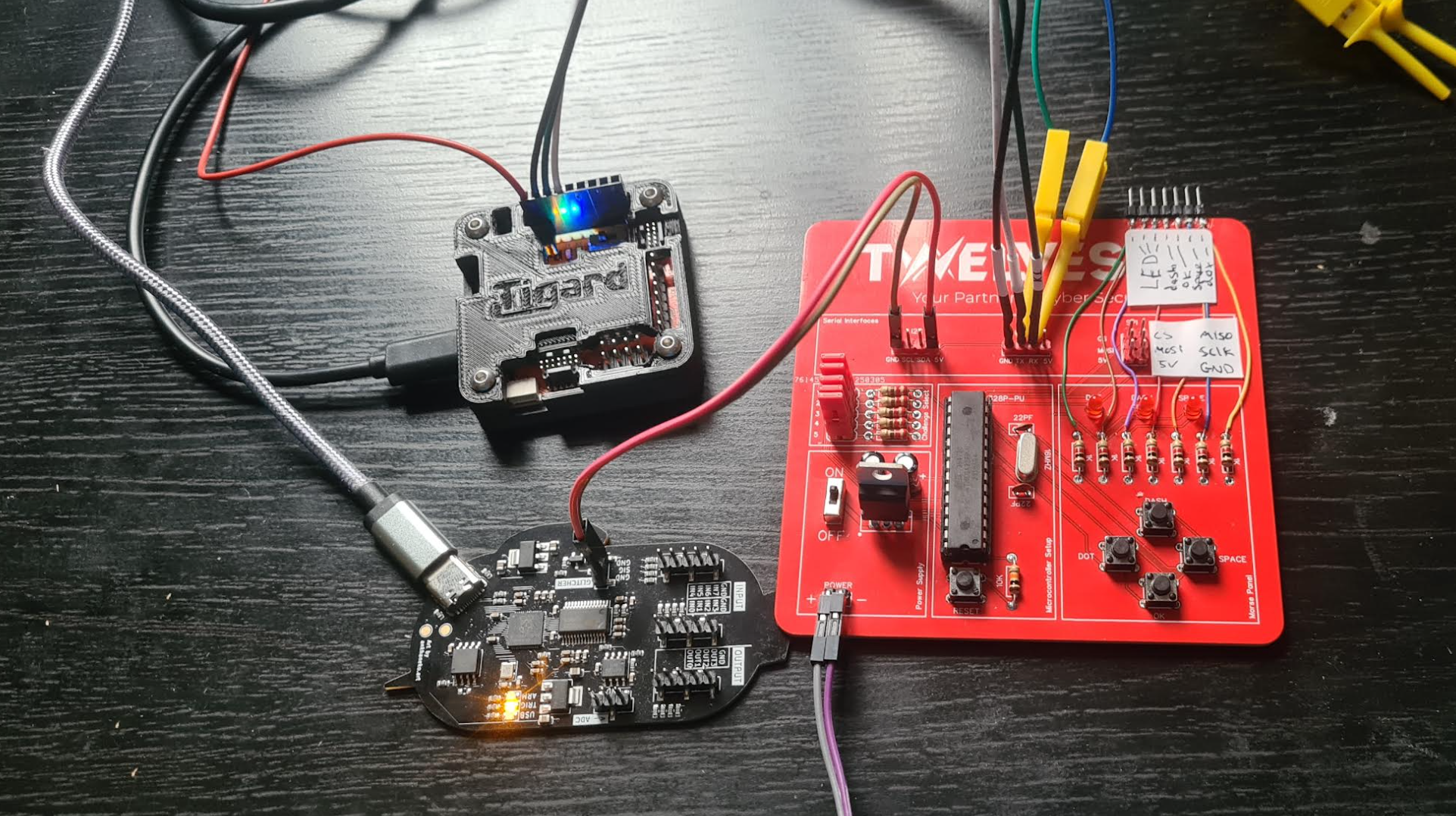
Notes
Start much like challenge #2 and analyze the traffic to identify the pulse width:
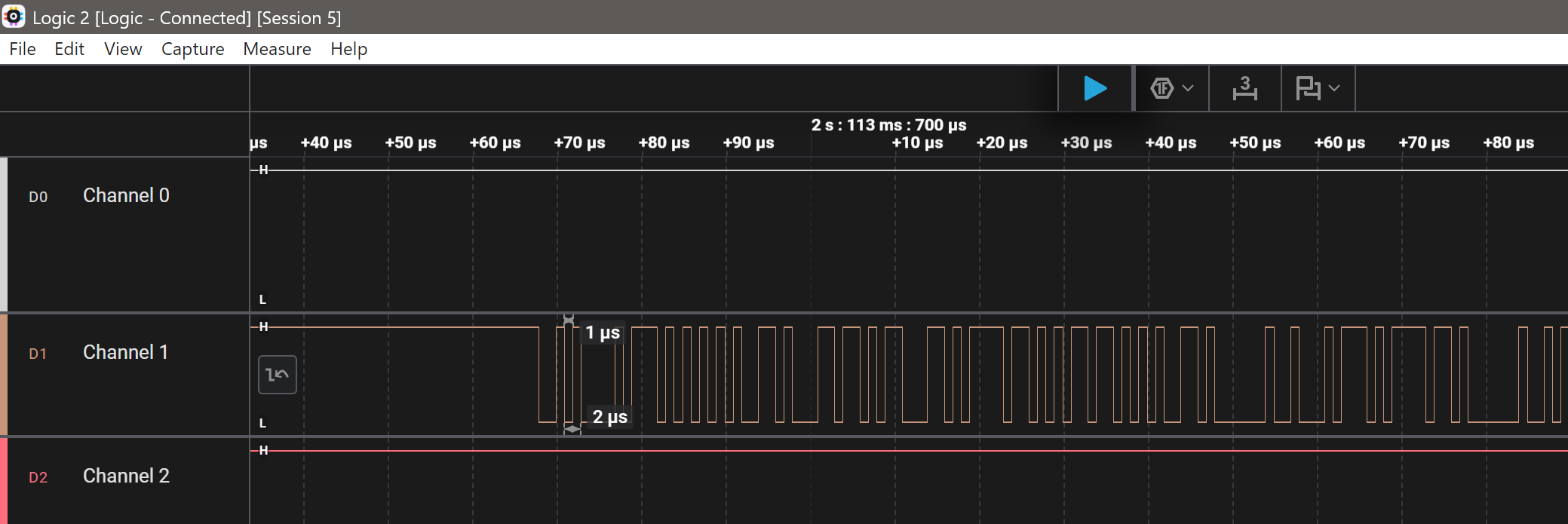
Quick math:
Baud rate = 1 / bit time
Bit time = 1 microsecond = 1 × 10⁻⁶ seconds
Baud rate = 1 / (1 × 10⁻⁶) = 1 000 000 baud
Answer: The UART baud rate is 1 000 000 baud (1 Mbps).
Lets check that:
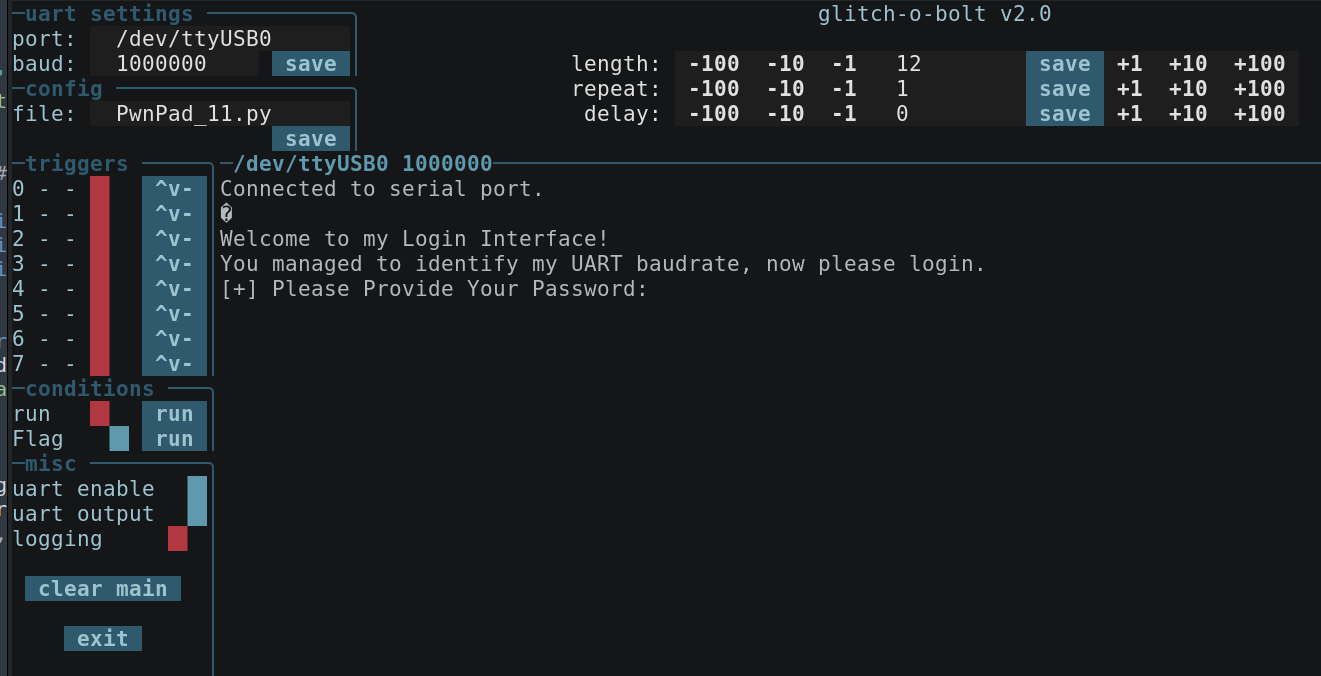
It already has a hardcoded password.
It sets a variable to 1 (the correct password variable).
You input a string and it will read up until "\r".
For each letter of the hardcoded password it will check the corresponding letter of the input string, if it doesnt match then it sets the variable to 0 (password incorrect).
Once this has complete it checks the variable and either returns the flag or an error message.
That looks as follows:
void blackbox_chain_UART_Glitch_Attack(void){
const char password[] = "-redacted-"; // orig 17 chars
Serial.begin(900847); // dbeef
Serial.println("\nWelcome to my Login Interface!");
Serial.println("You managed to identify my UART baudrate, now please login.");
Serial.println("[+] Please Provide Your Password:");
while(1){
Serial.flush();
if (Serial.available() > 0) {
char provided_password[strlen(password)];
Serial.readBytesUntil('\n', provided_password, strlen(password));
int success = 1;
for (int i = 0; i < strlen(password); i++) {
if (provided_password[i] != password[i]) {
success = 0;
break;
}
}
if (success == 1) {
Serial.println("-redacted flag-");
Serial.flush();
exit(0);
} else {
Serial.println("[-] Login FAILED");
Serial.println("[+] Please Provide Your Password:");
}
}
}
}
It seems like there are a few potential glitch places:
if (success == 1) { - have to get crazy lucky to glitch this comparison or glitch the variable “success” to be 1!
Serial.println("[-] Login FAILED"); - could glitch the pointer to the string and it echos another memory location (hopefully the flag) - insanely unlikley
for (int i = 0; i < strlen(password); i++) { - if could glitch the loop so skips over it entirely and “success” would stay 1
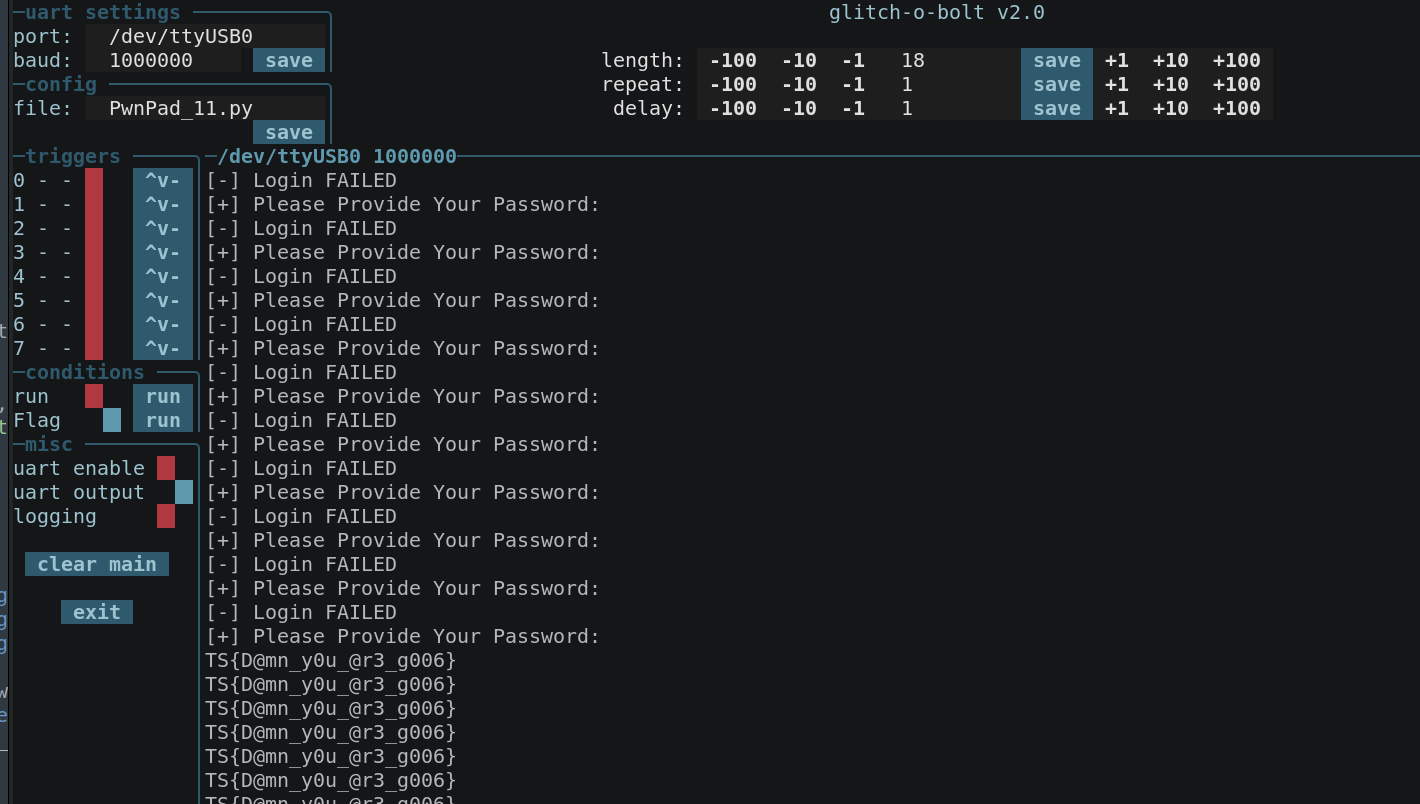
Of course I wrote a glitch-o-bolt script to brute-force this: 11_GoB_config.py
The watchdog is there because sometimes it glitched into a state that caused it to stop responding, if it doesnt respond for 2 seconds then the watchdog will restart the device (with a long glitch).
I didnt get it to bypass the check or echo the flag. I think given enough time it will, theres got to be a better way of doing this?
It did echo the previous challenges flag a lot (I guess it was in the memory, or at an address where one bit flip pointed to or somesuch)