GitBucket
GitBucket
|
initial commit
|
|---|
|
|
| FaultInjection/README.md 0 → 100644 |
|---|
| FaultInjection/examples/FaultyCat/01_simple_restart/cause_restart.png 0 → 100644 |
|---|
|
|
| FaultInjection/examples/FaultyCat/01_simple_restart/example_v1.0.ino 0 → 100644 |
|---|
| FaultInjection/examples/FaultyCat/01_simple_restart/example_v1.2_pretty.ino 0 → 100644 |
|---|
| FaultInjection/examples/FaultyCat/02_match_numbers/example_v2.0.ino 0 → 100644 |
|---|
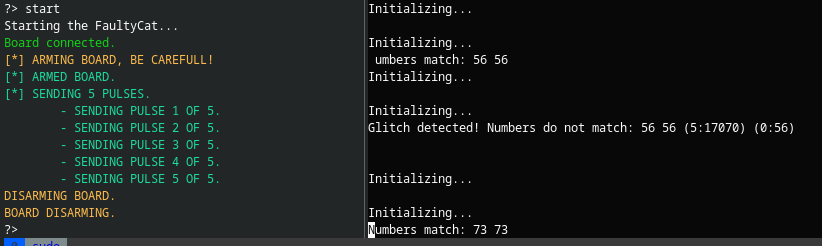
| FaultInjection/examples/FaultyCat/02_match_numbers/no_match.png 0 → 100644 |
|---|
|
|
| FaultInjection/examples/FaultyCat/03_password_check/attack.py 0 → 100644 |
|---|
| FaultInjection/examples/FaultyCat/03_password_check/example_v3.0.ino 0 → 100644 |
|---|
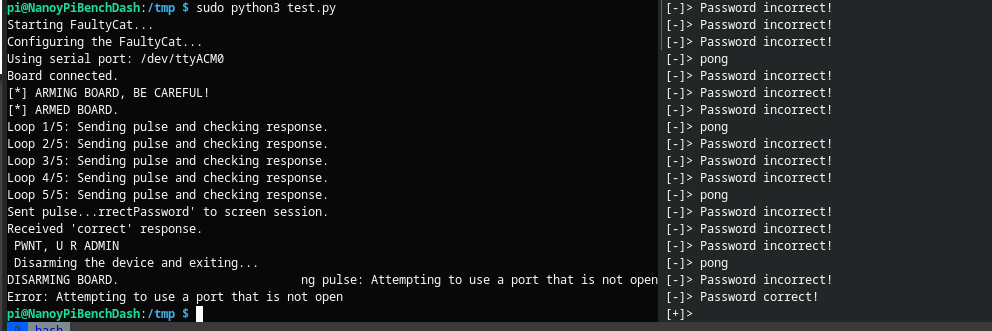
| FaultInjection/examples/FaultyCat/03_password_check/pass_correct_01.png 0 → 100644 |
|---|
|
|
| FaultInjection/prereqs/FaultyCat/Modules/CmdInterface.py 0 → 100644 |
|---|
| FaultInjection/prereqs/FaultyCat/Modules/ConfigBoard.py 0 → 100644 |
|---|
| FaultInjection/prereqs/FaultyCat/Modules/UART.py 0 → 100644 |
|---|
| FaultInjection/prereqs/FaultyCat/Modules/Worker.py 0 → 100644 |
|---|
| FaultInjection/prereqs/FaultyCat/Modules/__init__.py 0 → 100644 |
|---|
| FaultInjection/prereqs/FaultyCat/Modules/__pycache__/CmdInterface.cpython-37.pyc 0 → 100644 |
|---|
|
Not supported
|
| FaultInjection/prereqs/FaultyCat/Modules/__pycache__/ConfigBoard.cpython-37.pyc 0 → 100644 |
|---|
|
Not supported
|
| FaultInjection/prereqs/FaultyCat/Modules/__pycache__/UART.cpython-37.pyc 0 → 100644 |
|---|
|
Not supported
|
| FaultInjection/prereqs/FaultyCat/Modules/__pycache__/Worker.cpython-37.pyc 0 → 100644 |
|---|
|
Not supported
|
| FaultInjection/prereqs/FaultyCat/Modules/__pycache__/__init__.cpython-37.pyc 0 → 100644 |
|---|
|
Not supported
|
| FaultInjection/prereqs/FaultyCat/faultycmd.py 0 → 100644 |
|---|
| FaultInjection/prereqs/FaultyCat/requirements.txt 0 → 100644 |
|---|
| README.md 100644 → 0 |
|---|
| SideChannel/ATtiny85_Timing_Attack/4_digit.ino 0 → 100644 |
|---|
| SideChannel/ATtiny85_Timing_Attack/4_digit_attack.py 0 → 100644 |
|---|
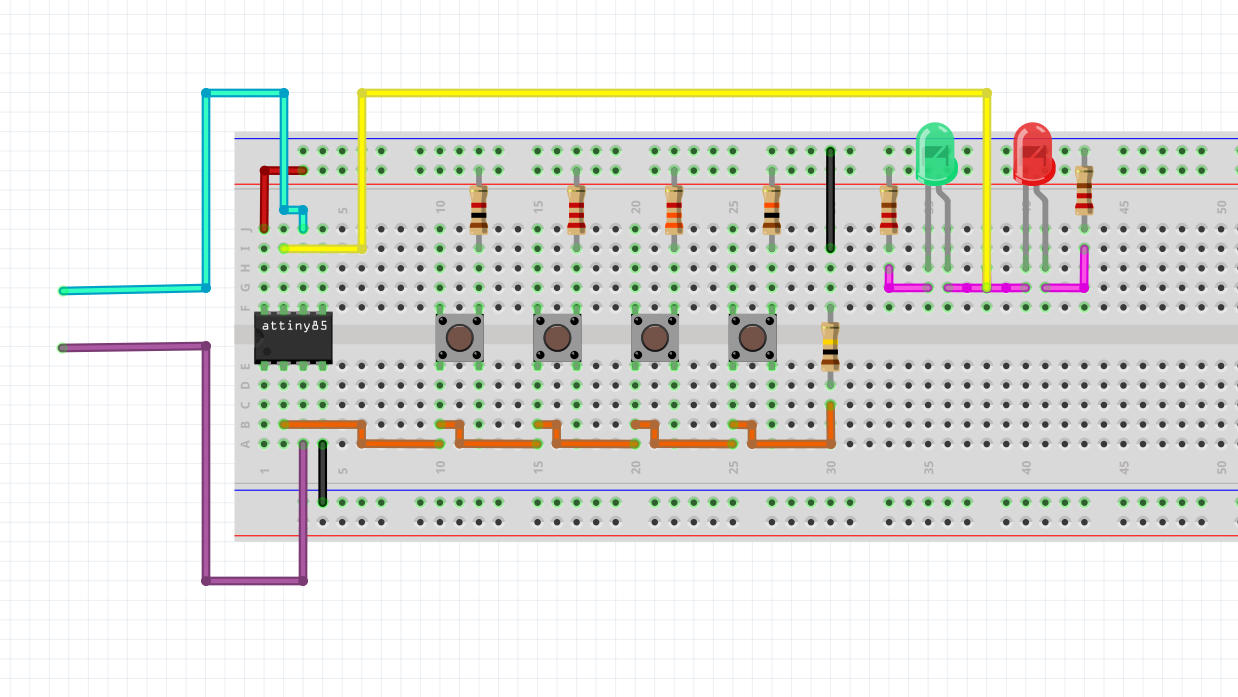
| SideChannel/ATtiny85_Timing_Attack/breadboard_setup.jpg 0 → 100644 |
|---|
|
|
| SideChannel/ATtiny85_Timing_Attack/multi_digit.ino 0 → 100644 |
|---|
| SideChannel/ATtiny85_Timing_Attack/multi_digit_attack.py 0 → 100644 |
|---|