GitBucket
GitBucket
|
Initial commit
|
|---|
|
|
| LdapUsrEnum-linux-386 0 → 100755 |
|---|
|
Not supported
|
| LdapUsrEnum-linux-amd64 0 → 100755 |
|---|
|
Not supported
|
| LdapUsrEnum-windows-386.exe 0 → 100755 |
|---|
|
Not supported
|
| LdapUsrEnum-windows-amd64.exe 0 → 100755 |
|---|
|
Not supported
|
| LdapUsrEnum.go 0 → 100755 |
|---|
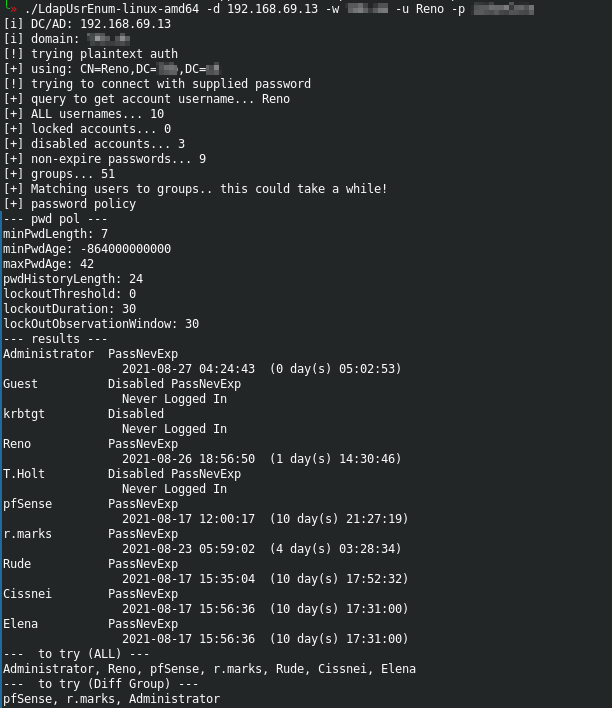
| LdapUsrEnum_Screenshot.png 0 → 100755 |
|---|
|
|
| go.mod 0 → 100755 |
|---|
| go.sum 0 → 100755 |
|---|