I would like to preface this by stating that I have no idea what I am doing, I am just playing and messing around and you probably shouldn’t take my word as gospel! That being said, I feel like I’ve learnt some things, hopefully you can from this blog also.
So I bought a couple of mini routers from amazon, thinking they would be prime targets for learning hardware hacking. Heres the listing for this router:
Yup at the time “OpenWrt” didn’t register in my brain and I was expecting something with custom stuff on it to pull and reverse! needless to say it was still a fun little device to play with.
Heres how it looks once you get it out of the box:


Nice, default wifi password of “goodlife”.
The first thing I did was plug in the USB and connect to the wifi, then load up the webpage to configure the device (http://192.168.8.1)
First it asks you the time, then to insert a password for the device, after that you can log in. There’s not much here really, standard router stuff. At the top right I notice “Advanced Settings” – Of course I go there. I’m greeted with another login page this time it asks for a username and password, but the username is pre-populated with “root”. I don’t know the root password, I figure I’d try the password I’d just created to access the basic web settings. It works! so I do a quick portsan of the routers IP (192.168.8.1) and find SSH open, low and behold I can login with the same root user and password.
I’m greeted with a “LEDE” banner, “LEDE Reboot 17.01.4 r3560-79f57e422d” specifically, so now I know the software in use, and that everything runs as root! It turns out this is a build of openwrt.
There’s not much to play with with the webapp or openwrt, I didn’t figure there would be, it’s open source so could have played with it to look for vulns without buying this router.
I originally noted that it’s running on lighttpd: 1.4.37 and running an out of date version of jQuery, again – pretty useless.
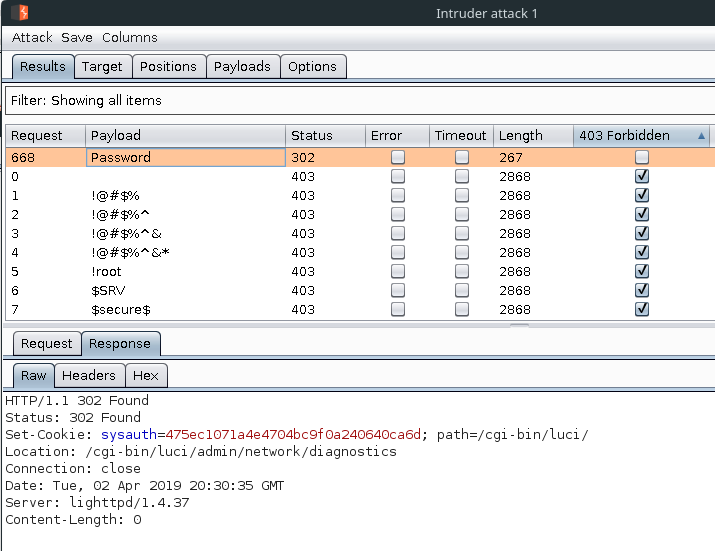
It turns out there’s no brute force protection on either of the login pages!
For the basic login page you have to request a token each time you try to log in, I couldn’t be bothered to script this up, especially when there’s no such protection on the advanced settings login page, as demonstrated below:
After having a play with the webapp for all of 2 seconds It’s time to open the box, it’s fairly simple, just a couple of plastic clips and the bottom falls off.
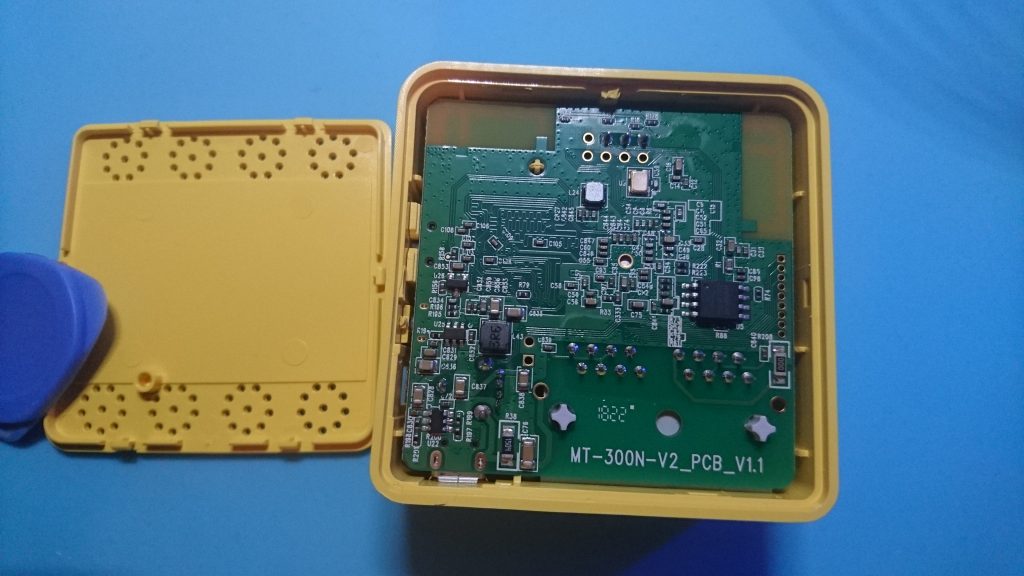

Heres some magnified pics of the chips, they might helps someone:


Hopefully you spotted the three male header pins that came attached to the PCB in the photo above, lets take a closer look:
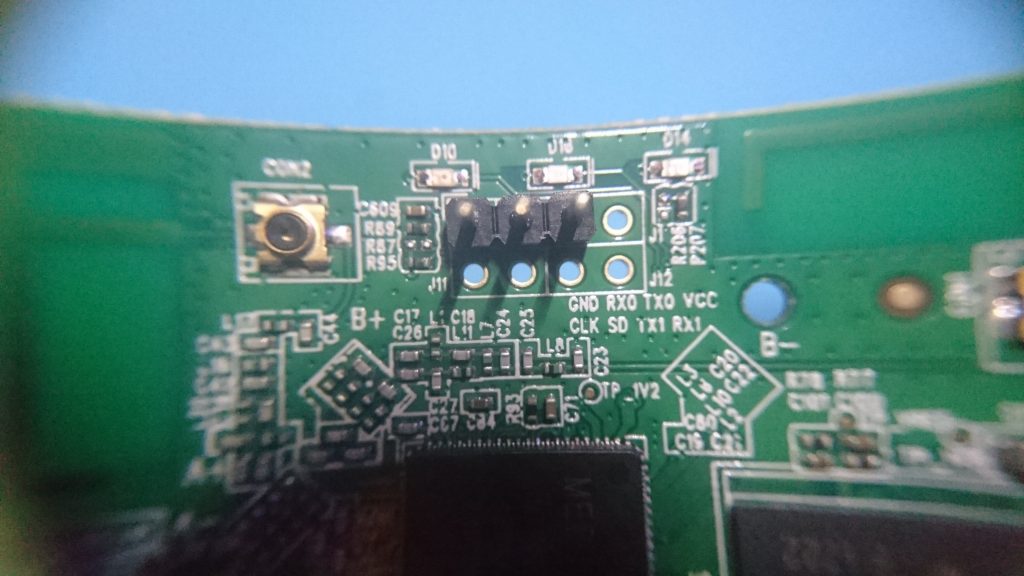
GND, RX0 & TX0 These seem a lot like serial to me, what a perfect excuse to pull out my new oscilloscope:
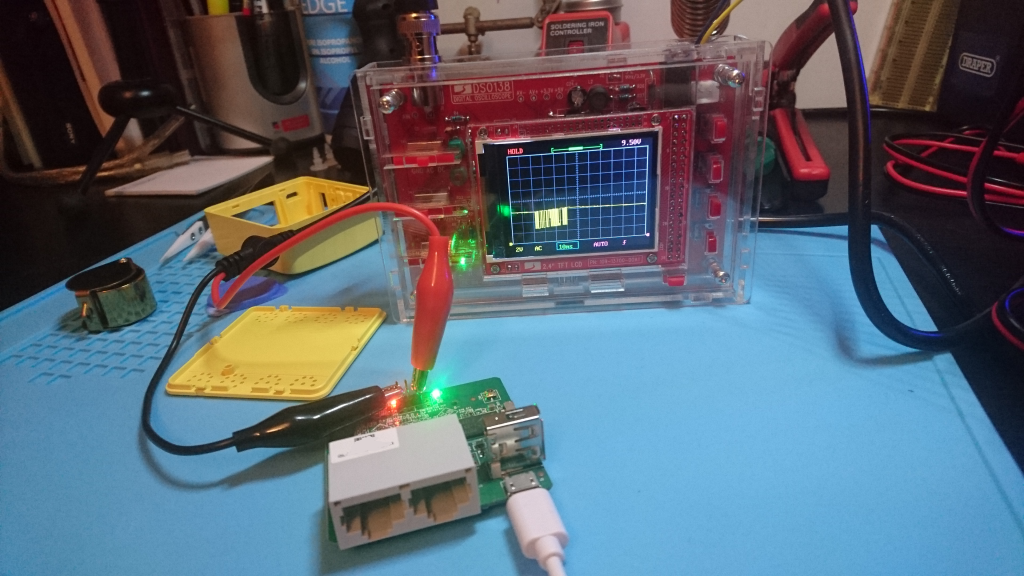
Yup that looks like data! Ok now lets get the USB->Serial cable out and find out what baud rate it’s running at!

To find the baud rate I used the script “baudrate.py” from https://github.com/biw/Baudrate.py the following command is how the script works
╰» ./baudrate.py -p /dev/ttyUSB1 -a |
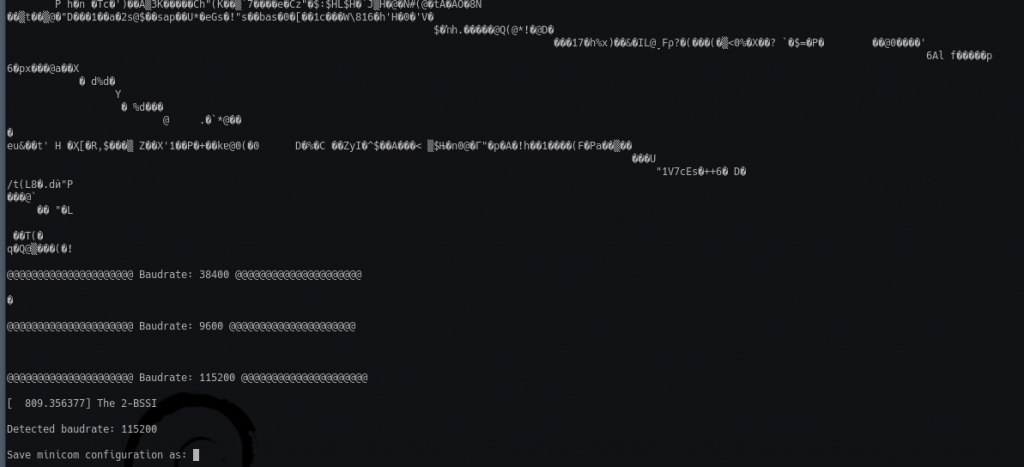
The following command is then used to see what is being transmitted over that serial port:
╰» screen /dev/ttyUSB1 115200 |
Which drops me into a root shell, no password needed!
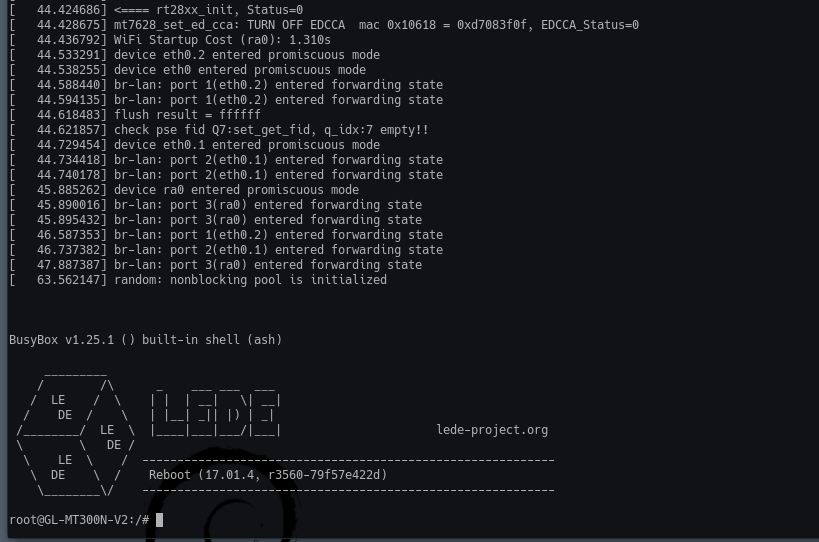
I then reboot the router a few times to see if I can get into the bootloader as I am suspicious that it should be possible, low-and-behold it is:
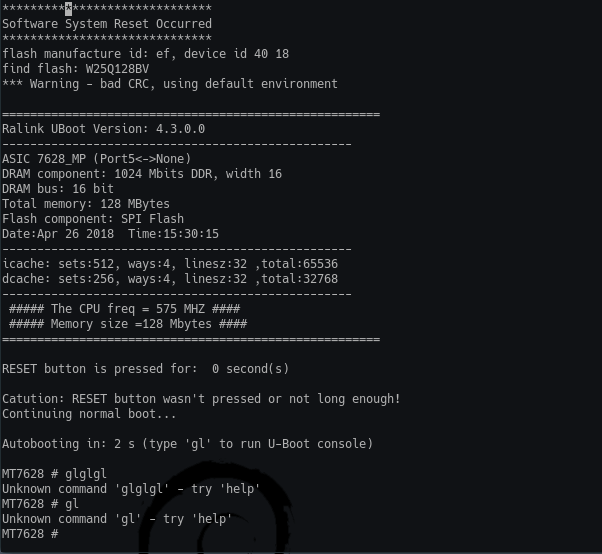
Well I didn’t expect this post to be this long and I have yet to show the hacks/mods I’ve done to this device. So I think I’ll end this here, I hope you’ve learnt something, I’ve certainly had fun so far.
Next up I do some hardware hacks/mods to this little router: GL iNet 300M Fun (Pt.2)
