All the code for this is available here: https://rossmarks.uk/git/0xRoM/Hardware
Fault injection is a technique in hardware penetration testing, used to assess and exploit vulnerabilities within physical devices by intentionally inducing errors or “faults” into a system. This enables us to understand how a device behaves under unexpected conditions, simulating potential attacks and stressors that might occur in real-world scenarios. By manipulating various environmental, electrical, or timing aspects of the hardware—such as introducing voltage spikes, clock glitches, or electromagnetic interference (as demonstrated in the previous blog) — testers can observe whether the device exhibits unintended behaviours, such as bypassing security mechanisms, leaking sensitive data, or revealing exploitable weaknesses.
Types of injection / glitching
Traditional Voltage Glitching
Traditional voltage glitching involves applying short, high-frequency voltage spikes or dips to a device’s power supply to disrupt its operations temporarily. In this approach, testers introduce controlled fluctuations in the power supply to induce faults, usually with the aim of causing the device to skip instructions, bypass security checks, or enter an unstable state. This type of glitching is often achieved by using a pulse generator to inject precise glitches into the power line, making it possible to create repeatable faults that can be tested and analysed. Traditional voltage glitching is widely used in assessing the security of embedded systems, particularly in devices where energy efficiency and cost constraints may leave power regulation vulnerable.
Crowbar Glitching
Crowbar glitching is a more aggressive variant of voltage glitching, where the power line of the device is intentionally shorted to ground for a very brief period, creating a sudden and sharp voltage drop. The “crowbar” technique gets its name from the idea of forcefully dragging the voltage down, similar to using a physical crowbar. Crowbar glitching is typically achieved by momentarily connecting the device’s power rail directly to ground, causing a rapid dip in voltage that can disrupt the device’s operation more intensely than traditional voltage glitches. This method is especially effective in bypassing bootloaders, secure boot processes, or cryptographic routines that might reset or enter a fail-safe mode due to the severe power fluctuation. Crowbar glitching requires careful timing and control, as the intense voltage drop can lead to permanent damage if not precisely applied.
Clock Glitching
Clock glitching involves injecting irregularities into the device’s clock signal, which governs the timing of its operations. By inserting deliberate delays or spikes into the clock pulses, testers can interfere with the synchronisation of processes within the hardware. A successful clock glitch may lead the device to skip instructions, improperly handle data, or even execute commands incorrectly. This is particularly valuable in assessing the resilience of microcontrollers, processors, and digital signal processors that depend on precise timing. For example, skipping an instruction during an authentication sequence might lead to security bypasses. Clock glitching is often used in testing systems with stringent timing requirements, like automotive and industrial controls, to verify that they handle timing disturbances gracefully.
Electromagnetic (EM) Fault Injection
Electromagnetic fault injection uses electromagnetic pulses to induce faults within a device by targeting specific circuits or components without direct electrical contact. By using focused EM pulses, testers can disrupt or interfere with the functioning of nearby circuits, causing unpredictable behaviour. This method is beneficial for identifying vulnerabilities that are challenging to induce with voltage or clock glitches, as EM faults can be targeted at precise areas within a chip or module. It’s especially effective for bypassing security protections in tamper-resistant hardware, such as smart cards and secure elements, where direct access to circuit lines may be restricted. The non-invasive nature of EM injection makes it valuable in scenarios where physical modification of the device is impractical.
Why choose crowbar glitching?
- Higher Disruption Potential: Crowbar glitching creates a more intense and abrupt voltage drop, which can effectively bypass critical security features, such as bootloaders and authentication routines, that might resist traditional voltage spikes.
- Precise Timing Advantage: The rapid nature of crowbar glitching allows for more targeted timing control, making it easier to disrupt specific instructions or security functions that rely on precise timing sequences.
- Increased Chance of Success in Secure Systems: For secure or tamper-resistant systems designed to handle minor voltage fluctuations, the sharper impact of crowbar glitching may be necessary to induce the desired fault, as traditional glitching might be insufficient.
- Targeted Fault Injection: By focusing the crowbar glitch on the specific chip’s power supply line, testers can induce faults without significantly affecting the power to other components. This selective application is especially useful in multi-component systems, allowing the glitch to focus on a single target chip (such as a microcontroller or secure element) without disturbing the overall system stability.
- Bypass Stronger Power Regulation: Devices with robust voltage regulation circuits are more resilient to traditional glitches. Crowbar glitching’s sudden and intense voltage drop can overwhelm these circuits, making it a viable approach for testing highly secure devices.
While crowbar glitching carries a higher risk of damaging components, its ability to induce intense, precisely-timed faults can make it more effective in penetrating advanced security features.
How it works
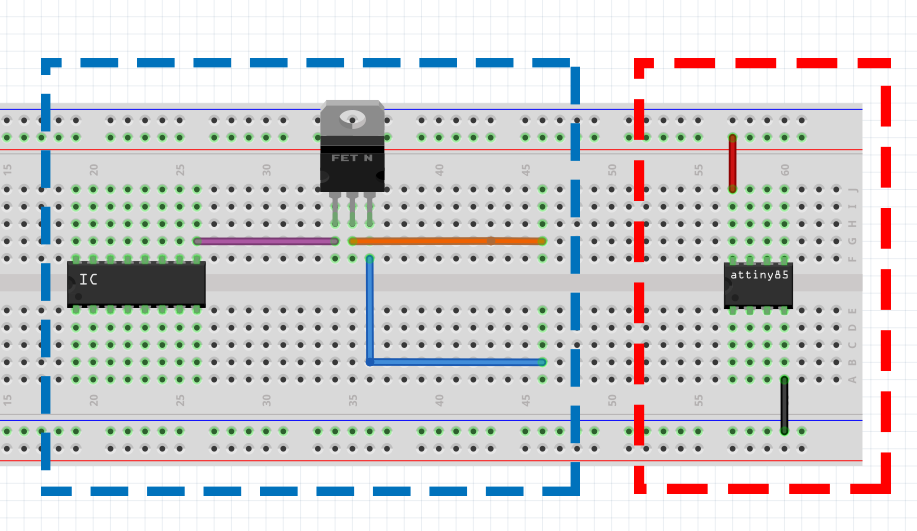
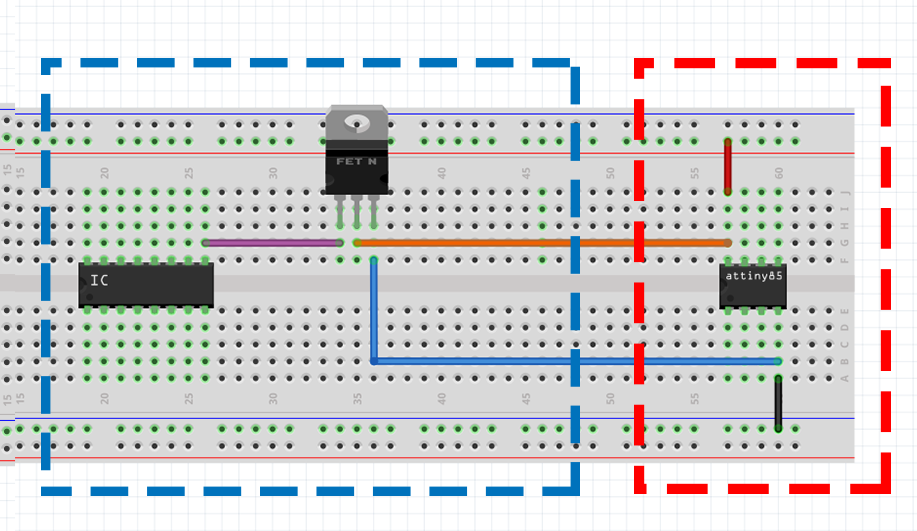
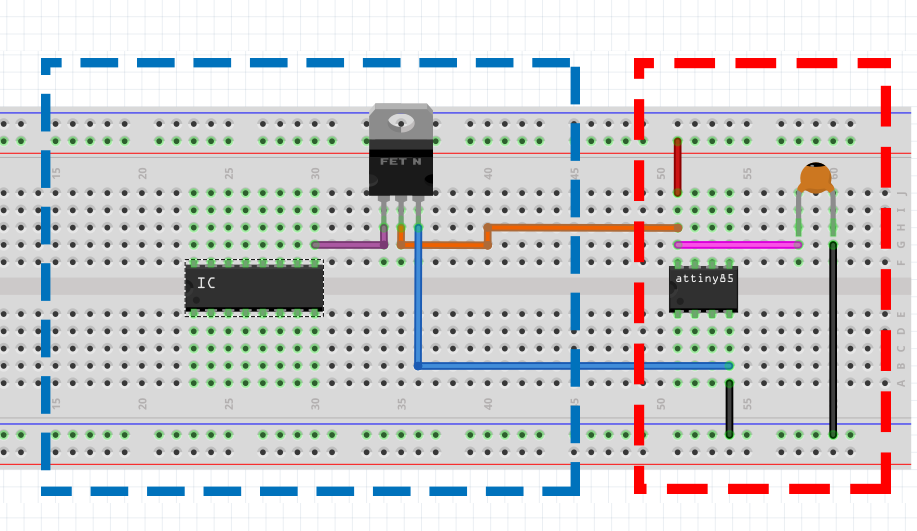
In the following image the device in the red box is the target device that we are wanting to cause a fault on. The device in the blue box is what we will be using to cause the glitch.
By connecting the “source” and “drain” to the power rail and ground of the target device we are able to cause a crowbar glitch. The circuit would look like this:
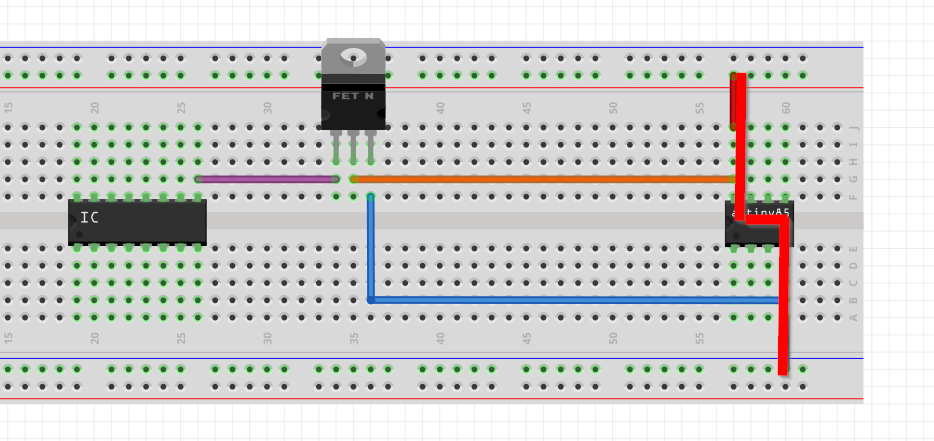
Under normal operation the power would have the following flow:
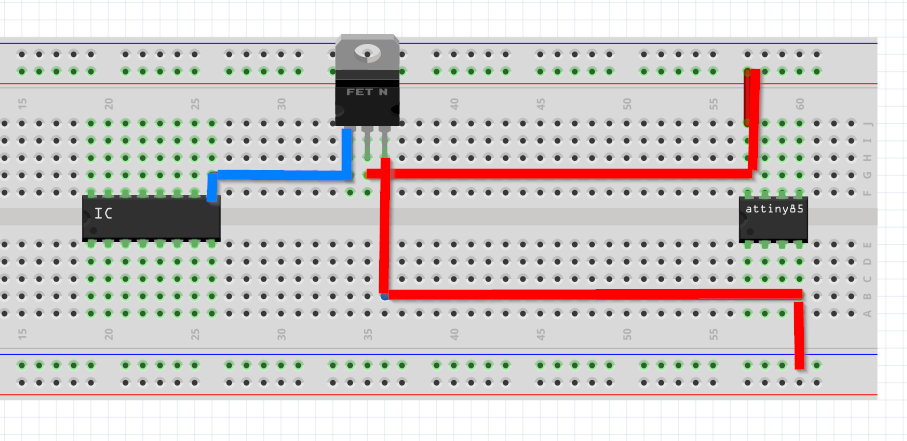
When we start to glitch by powering the gate of the mosfet the power follows this flow, temporarily disrupting the power to the chosen component:
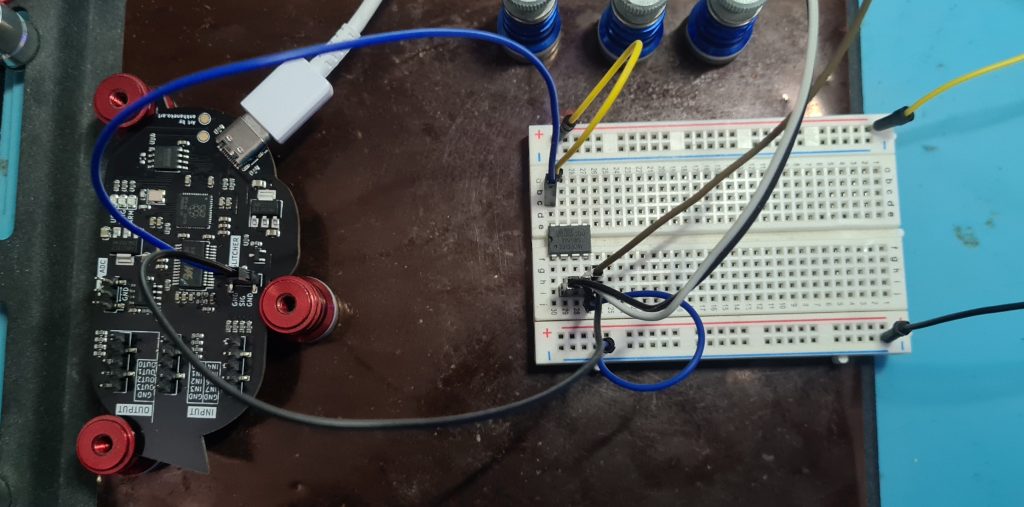
For my testing I used a “curious bolt” (which contains the mosfet controllable via python) and, as I did previously, I will be using the same Attiny85 as the target. Once it was all hooked up, it looked like this with the curious bolt on the left and the target on the breadboard to the right (the black and white wires go to a USB-UART for reading/writing to the serial debug of the chip):
Initial check
The first test was just to see if it works, the script was the same as the FaultyCat’s first example. When the device first starts it outputs “Initializing…” to the serial port. As demonstrated this worked, the script on the left causing the device to restart (on the right)
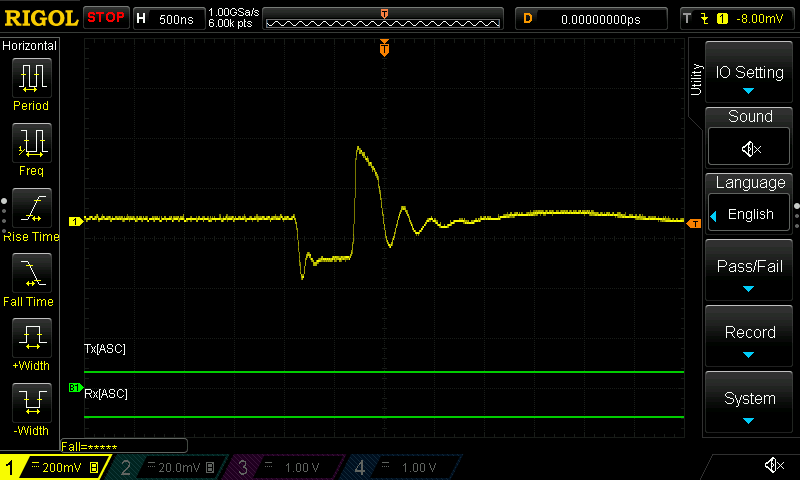
Heres how a glitch looks on the oscilloscope:
Test 01
This test was to see if it was possible to use this glitch to change the logic or running of the device without causing it to reset. All it does is create a random number, assign it to two variables, perform some operations on the variables which will still result in the same numbers but introduce a place for a glitch to occur and check the variables match (which they always should).
I could not get this to work, I couldn’t get the pulse for the glitch to be a short enough amount of time to cause a glitch and not a reset. Tom (one of the main devs/ the creator of the curious bolt?) explained the concept of the “bypass capacitor” which is common in electronics to keep the power stable. Put simply:
A bypass capacitor is a small capacitor placed across a power supply line and ground to smooth out fluctuations in voltage and prevent unwanted noise in electronic circuits. It acts as a local reservoir of charge that provides quick bursts of current when there’s a sudden demand, helping to maintain a stable voltage. When a circuit component, like a transistor or an integrated circuit, switches on and off, it can create small voltage spikes. The bypass capacitor shunts (or “bypasses”) these high-frequency signals to ground, preventing them from affecting other parts of the circuit.
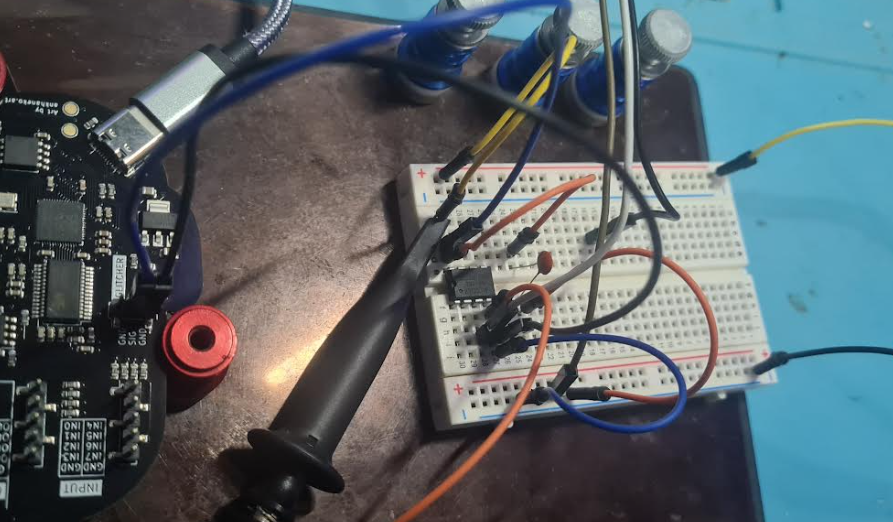
Heres how it looks in the fritzing schematic:
And here it is implemented on my breadboard:
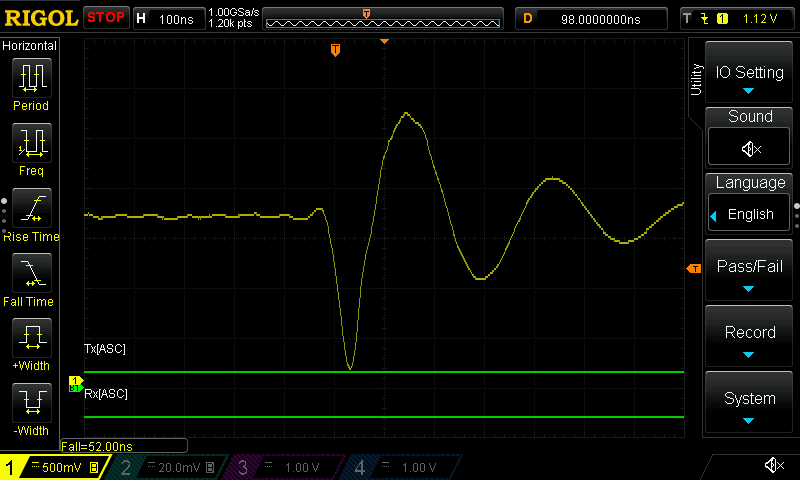
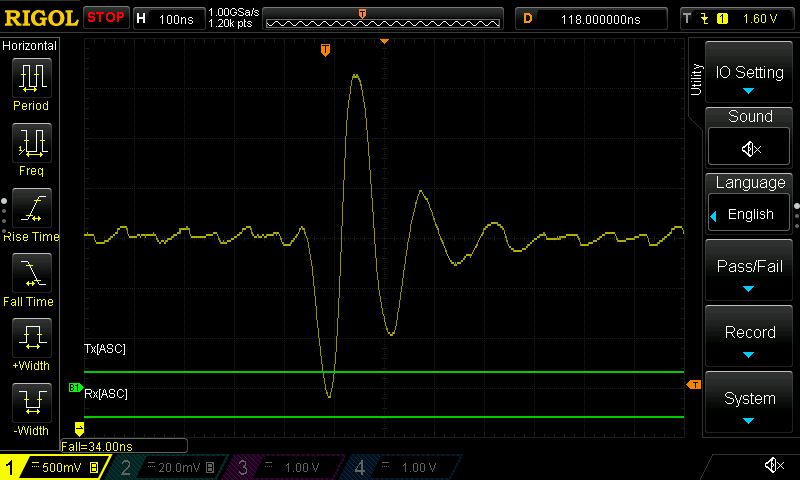
Heres how the power when glitching looks before and after:
In the second image the device recovers a lot quicker from the sudden power drop, this allowed me to cause the glitch without restarting the device as it spends less time without power!
If you are anything like me then you are probably wondering how that works since typically power goes in one pin and out the other, how does it go backwards? So heres a quick 3 stage process on how that works:
Voltage Difference: The capacitor has a voltage across it from being charged up by Vcc (one side at Vcc and the other at GND).
Glitch Drop: When the glitch lowers Vcc, the voltage on the capacitor’s Vcc side is suddenly higher than Vcc itself.
Automatic Discharge: Because electricity flows from high voltage to low voltage, the capacitor naturally pushes some of its stored charge back into Vcc to balance things out.
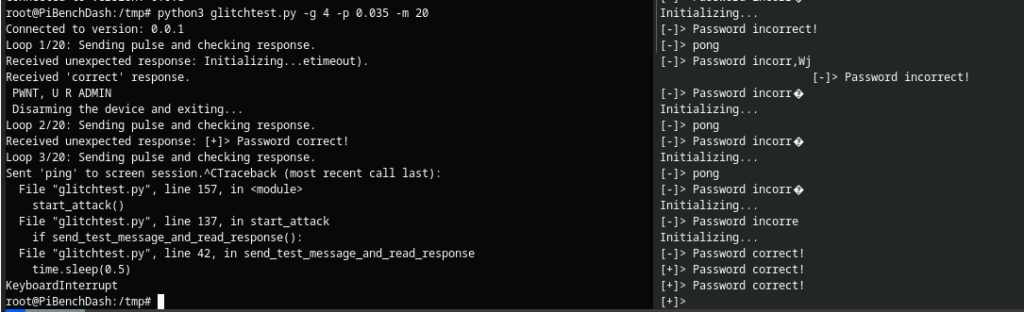
After loads of trial and error and changing timings I got the following:

The script on the left caused the device to glitch even though it seems the numbers appear to be the same! Since the numbers appear to be the same it is most likely that the glitch caused the device to skip over one of the comparisons:
// Check if the numbers still match after the potential glitch int match = 0; if (num1FirstDigit == num2FirstDigit) { if (num1SecondDigit == num2SecondDigit) { match = 1; } } if (match == 1) { Serial.print("Numbers match: "); Serial.print(num1); Serial.print(" "); Serial.print(num2); Serial.print("\r"); } else { Serial.print("Glitch detected! Numbers do not match: "); |
Test 02
This time the device was programmed to do the following:
- Output “Initializing…” when booting
- Start all output with “[-]” if not logged in or “[+]” if access is granted
- Reply “pong” when sent “ping” (to tell if device is alive or has crashed)
- Compare user input to password (to log in if anything sent other than “ping”)
The FaultyCat script to attack the same code was used but butchered to work with the CuriousBolt instead. The timings took so long to find, originally they were hardcoded in the script but it was becoming such a pain I ended up making them parameters to the script
(02-pass_match_glitch.py)
After much much tinkering, changing parameters and timings and double/triple checking connections eventually I got the following:
YEY the password had successfully been bypassed.
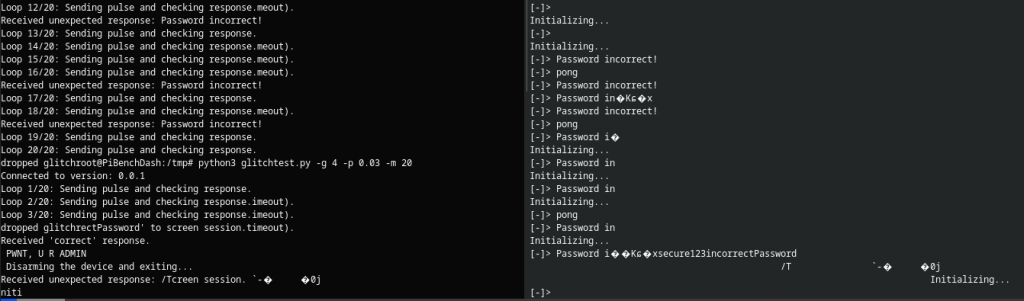
Much like when doing this with the FaultyCat sometimes it also vomited junk over the serial port
Well look at that! it’s echoed the password along with the incorrect one submitted by the script!
Conclusion
I think this demonstrates how useful this kind of attack can be. from my experience it’s more complicated to get working than EM fault injection, however once it’s dialled in it seems to be a lot more reliable.
Learning this and playing with it has been a lot of fun and I have to give a massive thank you to Tom and Aleph for helping with pointers and tips.
Now that I’ve got the concepts down it’s time to try the challenge board that came with the CuriousBolt, it contains 4 challenges!
Look how pretty the board is: