
Another short blog. Best be getting used to these by the looks of things. So again.. lying in bed and I decide to install another game to see how it works. I got a game called “Homeless?” It’s one of … Continue reading

Another short blog. Best be getting used to these by the looks of things. So again.. lying in bed and I decide to install another game to see how it works. I got a game called “Homeless?” It’s one of … Continue reading

So this is just going to be another short blog post. I was lying in bed playing one of my favourite games “SFCave”. I love it and have been playing for years. However there are some levels that I have … Continue reading

This is going to be a very short post. I wanted to play with some android apps and while roaming the play store came across a small app named “UnHackable” which only has a couple of hundred downloads. “Perfect” I thought, … Continue reading

I had the hypothesis that android IRC clients didn’t store credentials securely. Lets investigate… To decide what to look into I simply searched for “IRC” on the play store. The idea was to test as many as possible. I ended … Continue reading
This is not going to be the usual methodology (identification, assessment, exploitation, analysis) but more how I currently get from receiving a “scope of works” to the final report. Hopefully this will be useful to someone not yet in the … Continue reading
I don’t know about you, but I use a lot of programs and scripts that require using the command line. Mostly this is for security applications. However I have recently discovered “zenity” and wow! from wikipedia: “Zenity is free software … Continue reading

As a computer security person mostly, the other side of security is often overlooked by me (and probably others) this is just a small document to outline some physical risks for a company and things you should be awear of … Continue reading
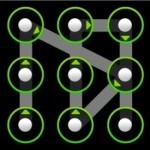
SO as you can probably tell from the title, this will be a small tutorial on how to get the password for android devices, specifically if it has a gesture password (see image left of here) For this demonstration I … Continue reading

Malware is unfortunately far too common to ignore or be unaware of in this day and age. However I am still asked every now and then about how it works and the differences between terms. So this article should hopefully remedy some … Continue reading

So I watched this talk the other day. It’s a brilliant talk, the recording is a bit quiet and I would recommend turning up the volume to watch it. If you are interested in the human aspect of security it’s a … Continue reading

Since I have gone over what I belive to be the merits of self-studying security, I have decided to go over some of the materials covered when trying to get certified in security, specifically the CEH (certified ethical hacker) Currently … Continue reading

You should now have a greater understanding of security and the various fields, what you would like to pursue and learn further, what your interested in or not. You have probably got some contacts and a list of resources that … Continue reading

The first part of this series on securing a LAMP server setup focused on hardening Apache (the popular web server) this article will focus on securing both MySQL and PHP. This is a fairly straight forward process and should be … Continue reading

Weather you are just starting out and want some basic tips or you have run a server for a while there comes a point when you realise a need for security on it, by default a lot of configurations are … Continue reading